[[{“value”:”
While no one is immune to cyber threats, smaller organizations with very limited security budgets face the task of managing risks and implementing timely remediation very often without the resources to buy and maintain multiple tools.
Security teams protecting these organizations have to choose approaches and tools that are flexible and address their most urgent needs.
When securing web-facing assets, for example, they can choose between a Dynamic Application Security Testing (DAST) platform like Intruder.io, a suite of testing tools like Pentest Tools, or an external attack surface management (EASM) platform like Attaxion.
Which Approach Is better?
In this article, we look at these three approaches and the three respective tools and consider the pros and cons of each option.
| Intruder.io | Attaxion | Pentest Tools | |
| Platform type | DAST | EASM | Suite of security testing tools |
| Price | Starts at $153 per month (for Cloud plan) | Starts at $129 per month | Starts at $85 per month |
| Strengths | Automated and continuous vulnerability scanningEmerging threat detectionIntegrations with popular tools and compliance platforms | Unmatched coverage in external asset discoveryAutomated, round-the-clock attack surface monitoringUses multiple risk scoring systems to rank threats | Customizable vulnerability scansComprehensive range of tools, including exploit tools |
| Weaknesses | More expensive than some alternativesUpdating scan targets can be tricky due to licensing rules | Has fewer direct integrations with ticketing and messaging toolsReports may offer less customization compared to some competitors | Limited automation in asset discoveryBasic prioritization capabilityLimited integration options in lower tiers |
Vulnerability Management With Intruder.io
Vulnerability management is the cyclical process of discovering, assessing, documenting, addressing, and tracking vulnerabilities to minimize risks.
While there are many vulnerability management solutions out there, Intruder.io is one of the most popular options.
Established in 2015, Intruder is a user-friendly, cloud-based vulnerability scanner and management platform designed to continuously monitor and automatically detect cybersecurity weaknesses across various digital assets including external and internal infrastructure, web applications, and APIs.
Cost
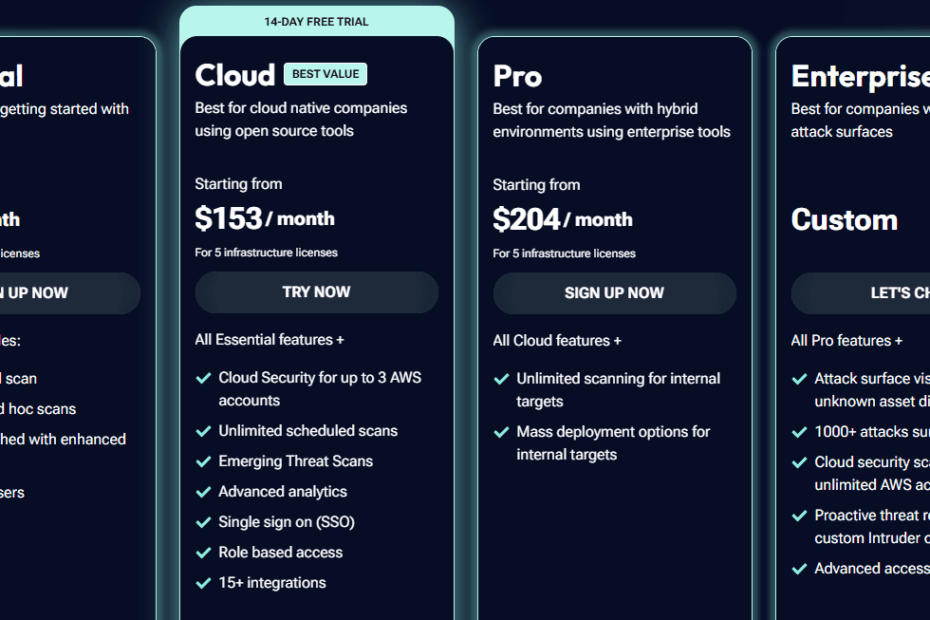
Intruder.io offers four pricing tiers: Essential, Cloud, Pro, and Enterprise. It offers a 14-day free trial period, but only for its Cloud tier.
The Essential plan, priced at $99 per month, only provides basic monthly network scans and comes with significant limitations it supports only one scheduled scan and doesn’t include any asset discovery capabilities, internal scanning, or attack surface monitoring.
The Cloud tier is a minimum viable choice for vulnerability management, starting at $153 per month, as it offers integrations with public clouds to automatically pull asset lists from them.
The Pro tier comes next, at $204 per month. Its only difference from the Cloud tier is that the Pro plan covers internal systems.
Attack surface monitoring, new service scans, subdomain discovery, and other premium features are only available for Enterprise users.
The price of this tier depends on the specific needs and scale of an organization, and interested parties need to contact Intruder.io directly.
Key Features
Asset Discovery
Intruder’s asset discovery capabilities on most plans are limited to cloud integrations and may not be as broad as what alternatives offer.
On the Cloud and Pro plans, users can connect their AWS, Microsoft Azure, Google Cloud Platform, and Cloudflare accounts, and Intruder can then detect hostnames and IP addresses within these environments and automatically add them as targets for vulnerability scanning.
More comprehensive asset discovery beyond the public cloud is available only on Intruder’s Enterprise plan, as this tier covers subdomains, related domains, and APIs that may not be part of the synced public cloud accounts.
Vulnerability Scanning
At its core, Intruder provides automated vulnerability scanning capabilities, allowing for both continuous and scheduled assessments to identify known security flaws.
On different plans, it offers different scanners – from OpenVAS and Nuclei to Tenable Nessus and OWASP ZAP.
A notable feature is its emerging threat scans, which proactively scan systems for newly disclosed vulnerabilities that could be relevant for your systems, thereby minimizing the window of exposure to potential attacks.
However, this feature is available only for subscribers of their Cloud, Pro, and Enterprise pricing plans.
Vulnerability Assessment And Prioritization
Intruder enriches scan results with enhanced risk data derived from threat intelligence sources such as the CISA Known Exploited Vulnerabilities (KEV) list and Exploit Prediction Scoring System (EPSS).
The platform also offers descriptions of the identified vulnerabilities, coupled with actionable remediation advice to facilitate efficient resolution.
Integrations
Intruder integrates with a wide array of popular development, collaboration, security, and ticketing systems, notably on all tiers except Essential. Here’s a list of all possible integrations:
- Slack
- Microsoft Teams
- GitHub
- GitLab
- ServiceNow
- Azure DevOps
- Zapier
- Okta
- AWS
- Google Cloud
- Azure
- Cloudflare
- Drata
- Vanta
- Microsoft Sentinel (Enterprise only)
Security Assessment With Pentest Tools
Penetration testing (pentesting) is a security assessment method that simulates an attack on an organization’s digital infrastructure.
Penetration testers identify vulnerabilities and then try to exploit them using the same techniques as threat actors.
They rely on a variety of tools, including commercial solutions like Pentest Tools, which provide automation, support, and advanced features.
Pentest Tools is a web-based platform that enables security teams to conduct penetration testing and vulnerability assessments efficiently and with minimal manual labor.
Cost
Pentest Tools provides five distinct plans: Free, Basic, Advanced, Teams, and Enterprise, which differ in the number of covered assets and feature scope.
Users have the option of choosing between monthly or yearly subscriptions, with a 15% discount offered for committing to an annual plan.
With the exception of the Free and Enterprise plans, all subscriptions come with a 10-day money-back guarantee, allowing new users to evaluate the service with minimal risk.
Key Features
Asset Discovery
Pentest Tools can discover assets, but by default, it doesn’t do so continuously or automatically take actions on found assets.
Instead, users have to run scans manually. It’s possible to automate at least some parts of the process, but it requires extra setup and effort.
To start asset discovery, users need to provide targets like IP addresses or domain names. Pentest Tools offers nine specific scanning tools, each performing a distinct reconnaissance task:
- Google hacking
- Website recon
- Web Application Firewall (WAF) detector
- URL fuzzer
- Domain finder
- Subdomain finder
- Port scanner
- Virtual host finder
The platform allows users to create scan templates, which bundle different tools into one.
Vulnerability Scanning
On top of the discovery tools, Pentest-Tools.com offers 11 vulnerability scanners and five exploit tools to identify security weaknesses across web applications, networks, and cloud environments.
It uses its own proprietary network scanner, which incorporates well-known open-source tools like OpenVAS, Sn1per, and Nuclei.
Users can set up automated robots to conduct batch scans (i.e., multiple assets are scanned in one go), though reports can only be generated for individual assets.
Vulnerability Assessment And Prioritization
Once an asset is scanned, Pentest Tools generates a list of findings, accessible from the “Findings” section. Issues are sorted by severity high, medium, low, or informational based on the CVSS score.
While Pentest Tools doesn’t offer custom prioritization criteria, its documentation mentions that it takes into account EPSS scores when adding detections to reduce false positives.
Users can manually adjust risk levels, allowing security teams to reclassify vulnerabilities with explanations.
Integrations
Pentest-Tools.com only offers integration options on its Teams and Enterprise plans, with lower-tier plans offering email notifications only.
Users on paid plans can automatically receive scan reports by email, while those on the Teams tier have more workflow integration options, including Jira, Microsoft Teams, Slack, Discord, and webhooks.
Integrations with cloud environments and compliance and risk management systems are also only available on the Teams and Enterprise plans.
External Attack Surface Management (EASM) With Attaxion
The two aforementioned approaches have their own limitations, primarily related to the scope of assets they deal with.
Vulnerability management focuses on identifying and addressing vulnerabilities within an organization’s known infrastructure, and penetration testing usually has an even more limited scope.
In contrast, EASM takes a broader, outside-in perspective. It involves continuously discovering, monitoring, and analyzing all Internet-facing digital assets of an organization including assets that might be unknown and unmanaged (e.g., shadow IT).
One EASM platform we examine is Attaxion, a modern, cloud-based EASM tool engineered to provide security teams of all sizes with comprehensive visibility, continuous monitoring, and automated control over their entire external-facing digital footprint.
Cost
Like Intruder, Attaxion has four pricing plans: Starter ($129/month), Plus ($349/month), Business ($949/month), and Enterprise (custom price).
However, the difference from other tools is that all Attaxion features are accessible on all tiers, and the price only goes up as the organization’s asset count increases.
Attaxion also offers a 30-day free trial period that includes all features. Customers who choose to pay annually can get two months free.
Key Features
Asset Discovery
Attaxion uses various cyber reconnaissance techniques to automatically discover and catalog all Internet-facing assets, including domains, subdomains, IP addresses, cloud resources, and even exposed email addresses.
These advanced asset discovery capabilities allow Attaxion to regularly identify assets that organizations were previously unaware of.
The platform’s asset-to-asset mapping helps visualize the relationships and dependencies between these assets, providing a comprehensive understanding of the external attack surface and potential attack paths.
Vulnerability Scanning
Attaxion automatically scans all discovered assets for known and emerging vulnerabilities, weaknesses, and other security issues.
Among other things, it relies on a well-known open-source scanner (OWASP ZAP) for web application scanning. It also performs port scanning and technology fingerprinting.
It offers both passive and active scanning methods, with the option to switch between the two.
| Passive scanning methods | Active scanning methods |
| WHOIS LookupPassive Subdomains LookupReverse DNS LookupReverse WHOIS LookupIP Geolocation LookupIP Netblocks LookupCloud Providers ScannerDNS Lookup | Vulnerability ScannerWeb CrawlerActive Subdomains ScannerSSL LookupPort ScannerScreenshot Lookup |
Vulnerability Assessment And Prioritization
Attaxion employs intelligent risk prioritization by integrating multiple vulnerability scoring parameters, including CVSS, EPSS score, and CISA KEV data, to help security teams focus on the most critical and exploitable issues.
To help speed up remediation, Attaxion provides detailed context and actionable guidance for each identified security issue.
Integrations
For seamless integration into existing workflows, Attaxion offers integrations with tools like Slack and Jira for alerts and ticket creation, as well as with major cloud providers (AWS, Google Cloud, Microsoft Azure, and DigitalOcean) for automated asset synchronization.
Enterprise clients can request custom integrations.
Intruder vs Pentest Tools vs Attaxion: What To Choose?
The choice between Intruder.io, Pentest Tools, and Attaxion depends largely on an organization’s specific security needs and priorities.
- Intruder.io offers a strong focus on vulnerability management with its automated and continuous scanning. It is a user-friendly, cloud-based platform that integrates with other systems.
- However, it’s the costliest tool of those reviewed in this article, and its asset discovery capabilities are limited to cloud sync on the lower-priced tiers (with the exception of the Essential plan where Intruder doesn’t offer any asset discovery at all).
- Pentest Tools provides a comprehensive suite of penetration testing tools. It is a good option for security teams that need to conduct in-depth security assessments and offers customizable scans and a range of tools.
- Its pricing is also competitive. However, it requires more manual effort, particularly in asset discovery, and its automation capabilities do not work out of the box as those of Intruder.io or Attaxion.
- Pentest Tools, as suggested by the name, is primarily targeted at red teams.
- Its pricing is also competitive. However, it requires more manual effort, particularly in asset discovery, and its automation capabilities do not work out of the box as those of Intruder.io or Attaxion.
- Attaxion distinguishes itself with its external attack surface management (EASM) approach.
- It excels in automatically discovering and monitoring an organization’s entire external-facing digital footprint, including previously unknown assets.
- Its key strengths lie in its broad asset discovery and intelligent risk prioritization.
- While its reporting capabilities may not be as flexible as those of Pentest Tools, Attaxion offers full visibility into your external attack surface and comes with very competitive pricing.
- Its key strengths lie in its broad asset discovery and intelligent risk prioritization.
- It excels in automatically discovering and monitoring an organization’s entire external-facing digital footprint, including previously unknown assets.
For organizations with large security budgets, using all three tools together could be beneficial, as they have different focus areas: Attaxion excels at discovery, Intruder has the best UI and great reporting, while Pentest Tools enables proper pentesting and red teaming.
However, those with limited headcounts and budgets usually need to choose just one tool.
They may want to prioritize continuous and comprehensive visibility of their external attack surface and proactive identification of potential threats across it.
For this goal, Attaxion is the most suitable of the three.
Its robust asset discovery, coupled with continuous vulnerability scanning and solid risk prioritization capabilities, provides a strong foundation for maintaining a strong security posture.
The post Intruder vs. Pentest Tools vs. Attaxion: Selecting The Right Security Tool appeared first on Cyber Security News.
“}]]
Read More Cyber Security News