[[{“value”:”
A sophisticated new ransomware strain dubbed “Lyrix” has emerged in the cyberthreat landscape, targeting Windows systems with an arsenal of advanced evasion techniques that have caught the attention of security researchers worldwide.
The malware represents a significant evolution in ransomware development, incorporating machine learning-based detection avoidance and novel persistence mechanisms that challenge traditional security approaches.
Initial reports suggest the ransomware has already compromised several enterprise networks across North America and Europe, with attackers demanding ransom payments ranging from $50,000 to $2 million depending on the target organization’s size and perceived ability to pay.
The attack campaign appears to leverage a multi-vector approach, with threat actors primarily exploiting unpatched vulnerabilities in public-facing applications, particularly those running outdated versions of Microsoft Exchange Server and VMware vCenter.
Secondary infection vectors include spear-phishing campaigns targeting system administrators with weaponized attachments disguised as security patches or software updates.
The ransomware’s operators have demonstrated sophisticated social engineering capabilities, often conducting preliminary reconnaissance on target organizations through LinkedIn and corporate websites to craft highly convincing phishing messages.
Cyfirma researchers identified the malware’s unique characteristics during their analysis of recent attack patterns, noting that Lyrix employs a previously unseen technique called “behavioral chameleon mode.”
.webp)
This allows the ransomware to alter its execution patterns based on the security tools detected in the target environment.
The malware’s impact extends beyond typical file encryption, as it systematically targets backup systems, shadow copies, and recovery partitions before initiating its primary encryption routine.
Organizations affected by Lyrix have reported complete system paralysis, with recovery times extending beyond two weeks even when backups were available.
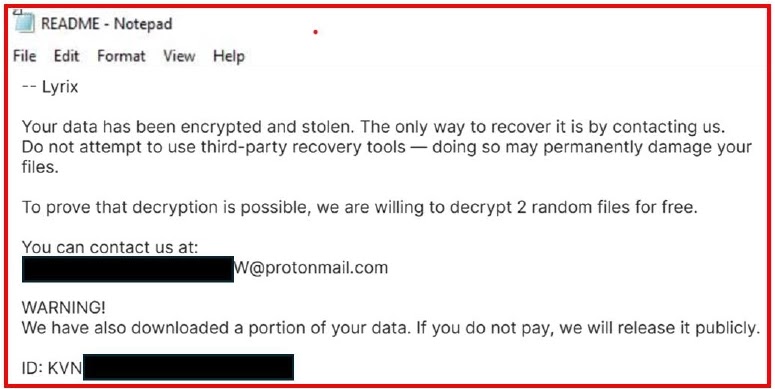
The ransomware’s operators have established a dark web presence through multiple Tor-based leak sites, where they threaten to publish stolen data if ransom demands are not met within 72 hours.
Intelligence suggests the group behind Lyrix may have connections to other prominent ransomware families, as evidenced by shared code signatures and similar communication protocols.
.webp)
The emergence of this threat coincides with a broader trend of ransomware groups adopting more sophisticated evasion tactics to counter improving corporate cybersecurity defenses.
Advanced Persistence and Detection Evasion Mechanisms
Lyrix demonstrates remarkable sophistication in its persistence mechanisms, utilizing a technique researchers have termed “registry time-bombing.”
The malware creates seemingly legitimate registry entries that execute dormant code at predetermined intervals, making detection significantly more challenging for traditional antivirus solutions.
The ransomware employs a multi-stage loader that injects its primary payload through legitimate Windows processes such as explorer.exe and svchost.exe.
This process injection technique utilizes the following approach:-
HANDLE hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, targetPID);
LPVOID pRemoteCode = VirtualAllocEx(hProcess, NULL, payloadSize,
MEM_COMMIT, PAGE_EXECUTE_READWRITE);
WriteProcessMemory(hProcess, pRemoteCode, payload, payloadSize, NULL);
CreateRemoteThread(hProcess, NULL, 0, pRemoteCode, NULL, 0, NULL);The malware’s evasion capabilities include runtime packing with custom cryptographic algorithms that change encryption keys every 24 hours, effectively creating a moving target for signature-based detection systems.
Additionally, Lyrix monitors for analysis environments by checking for specific registry keys, file paths, and running processes commonly associated with security research tools, immediately terminating execution if detected.
Celebrate 9 years of ANY.RUN! Unlock the full power of TI Lookup plan (100/300/600/1,000+ search requests), and your request quota will double.
The post New Lyrix Ransomware Attacking Windows Users With New Evasion Tactics appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News