[[{“value”:”
Business Email Compromise (BEC) attacks don’t need malware to do damage. All it takes is one convincing message; a fake login prompt, a cleverly disguised link, and an employee’s credentials are gone.
From there, attackers can quietly access inboxes, exfiltrate sensitive documents, and impersonate executives for financial fraud.
The worst part is that these attacks are often missed by standard email filters and antivirus tools.
That’s why security teams are turning to solutions like interactive sandboxing to catch what automated tools can’t.
What Makes BEC So Hard To Detect?
Business Email Compromise doesn’t leave obvious digital fingerprints. Instead, it hides in plain sight, using clean infrastructure, normal-looking messages, and subtle social engineering.
Here’s why they often go unnoticed:
- Well-hidden intent – No malware, just links disguised as routine business.
- Trusted platforms – Hosted on services like OneDrive or Google Forms, which rarely raise flags.
- Redirect chains – Multiple hops before the real phishing page appears.
- CAPTCHAs and blockers – Designed to stop bots and automated scanners in their tracks.
- Human-first tactics – Relies on social pressure, not code execution.
- Context-aware messages – Tailored with names, roles, and internal language to avoid suspicion.
The Fastest Way To Spot A BEC Attack
When time is critical, waiting hours for a verdict just won’t cut it. Interactive sandboxes give security teams the power to investigate suspicious files or URLs in minutes, not hours or days.
Instead of relying on static scans or logs, analysts can watch the attack unfold in real time, interact with it like a real user would, and uncover the full scope of the threat.
To show how this works in practice, let’s take a look at a real-world phishing attack detonated inside ANY.RUN’s Interactive Sandbox.View analysis session with attack

This attack starts with a seemingly harmless email containing a large green “Play Audio” button, a common lure used by the Tycoon2FA phishing kit, one of the most widespread threats in corporate environments today.
Here’s how the sandbox reveals the full chain:
1. Opening The Email In A Safe VM
The email is uploaded to the sandbox and opened inside a fully isolated Windows environment. The analyst can safely click the “Play Audio” button to see what happens next, no risk to their real system.

2. Following The Redirect Chain
Before starting the analysis, users can enable Automated Interactivity, a feature in ANY.RUN that simulates real user behavior, like clicking buttons, solving CAPTCHAs, and navigating redirects.
Once turned on, the sandbox takes over these repetitive tasks automatically, allowing analysts to observe the full attack flow without manual input.
Equip your team with real-time phishing detection, automated analysis, and full attack chain visibility — all in one interactive sandbox.– Join ANY.RUN now
In our example, clicking the “Play Audio” button triggers a series of redirects, a classic evasion technique used to obscure the final phishing destination.
Eventually, a CAPTCHA challenge appears, designed to block automated scanners.

But with Automated Interactivity enabled, ANY.RUN handles this seamlessly, solving the CAPTCHA and continuing the analysis flow, saving valuable time and reducing workload.
The sandbox reaches the final phishing page within seconds, without any manual effort, making it ideal for fast triage or high-volume alert queues.
3. Reaching The Final Phishing Page
After solving the CAPTCHA, the sandbox lands on a fake Microsoft login page; clean design, familiar branding, but a suspicious URL full of random characters and a missing favicon.
Red flags a user might miss but the sandbox doesn’t.

4. Exposing The Technical Details
Interactive sandboxes like ANY.RUN map out the entire attack chain so your team can understand exactly how the threat works and where to respond.
Here are a few details the sandbox revealed in this session with Tycoon attack:
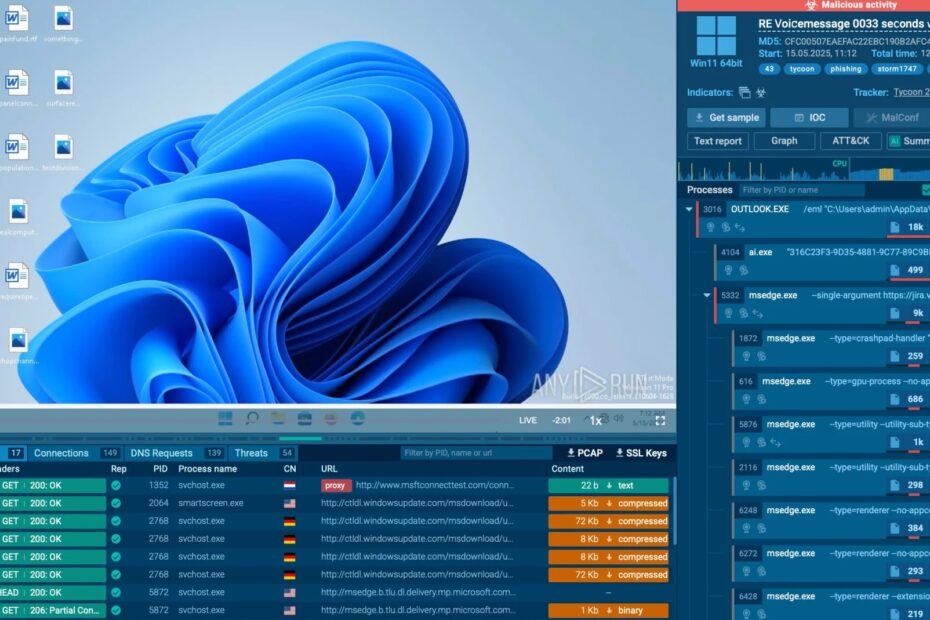
Full Process Tree
In this case, the process tree clearly flagged a suspicious browser process initiated after clicking the “Play Audio” button. It was labeled as Phishing, with subprocesses showing browser redirects and script execution.

The process tree inside ANY.RUN provides a step-by-step breakdown of how the phishing page was reached, giving teams the visibility needed to trace multi-stage BEC threats that often hide in user actions.
Network Requests: The sandbox captured every HTTP/HTTPS request, including redirect URLs and the final phishing domain, a fake Microsoft login page hosted on a random, non-branded domain.

We see how the sandbox exposes the full attacker infrastructure behind the Tycoon2FA kit, allowing teams to block malicious endpoints and understand how the phishing campaign is set up.
Suricata Alerts :During the session, a Suricata rule fired: “PHISHING [ANY.RUN] Suspected Tycoon2FA’s Phishing-Kit Domain”.

This alert instantly validates the threat with a specific detection signature, speeding up the decision-making process and allowing security teams to respond with confidence.
Tagged Verdict : ANY.RUN automatically tagged the sample as linked to the Tycoon2FA phishing kit, identifying the campaign behind the fake login flow.

Eliminates guesswork and ensures fast triage; even junior analysts can quickly classify and report on the threat without deep manual investigation.
How Interactive Sandbox Helps You Stay Ahead Of BEC Threats
Interactive sandboxing gives teams the context, visibility, and speed they need to detect and respond to Business Email Compromise threats before they escalate.
Here’s how ANY.RUN delivers that advantage:
- Live visibility into threat behavior
Watch the full attack chain unfold, from the initial lure to redirects, CAPTCHA challenges, and the final phishing page, in real time.
- Faster, more confident decisions
Get an initial verdict in under 40 seconds, with behavioral evidence to support faster triage and response.
- Automated Interactivity to reduce workload
Automate common user actions like clicking buttons, solving CAPTCHAs, and following redirects. This saves time and helps analysts focus on higher-level decision-making.
- Cloud-based, no setup required
Analyze files and URLs in a secure virtual environment from anywhere, no infrastructure maintenance or local configuration needed.
- Centralized IOC collection
Collect and export domains, IPs, URLs, file hashes, and other indicators of compromise in one click, ready for blocking, reporting, or enrichment.
- Built-in threat classification
Get immediate context with labeled processes, triggered Suricata rules, and campaign-level tagging (e.g., Tycoon2FA) to speed up identification.
- Supports all analyst skill levels
Whether it’s a junior SOC analyst or a senior threat hunter, ANY.RUN offers an intuitive interface and detailed reporting to support investigation, learning, and collaboration.
- Improves security workflows
Reduces alert fatigue, shortens incident response time, and helps teams prioritize real threats over false positives.
Equip your team with the solution to detect sophisticated phishing threats in real time, reduce analyst workload, and respond with confidence: Join ANY.RUN to experience its full capabilities for 14 days → The post Business Email Compromise Attacks: How To Detect Them Early appeared first on Cyber Security News.
“}]]
Read More  Cyber Security News
Cyber Security News