[[{“value”:”
Threat actors are allegedly offering the complete source code of a sophisticated Malware-as-a-Service (MaaS) botnet for sale.
This advanced malicious framework represents a significant escalation in cybercriminal capabilities, leveraging legitimate enterprise-grade technologies and blockchain integration to create a highly resilient and scalable attack platform.
Stealthy Architecture of Botnet
The botnet’s technical foundation demonstrates remarkable sophistication, built upon a stack of legitimate software frameworks that security solutions often overlook.
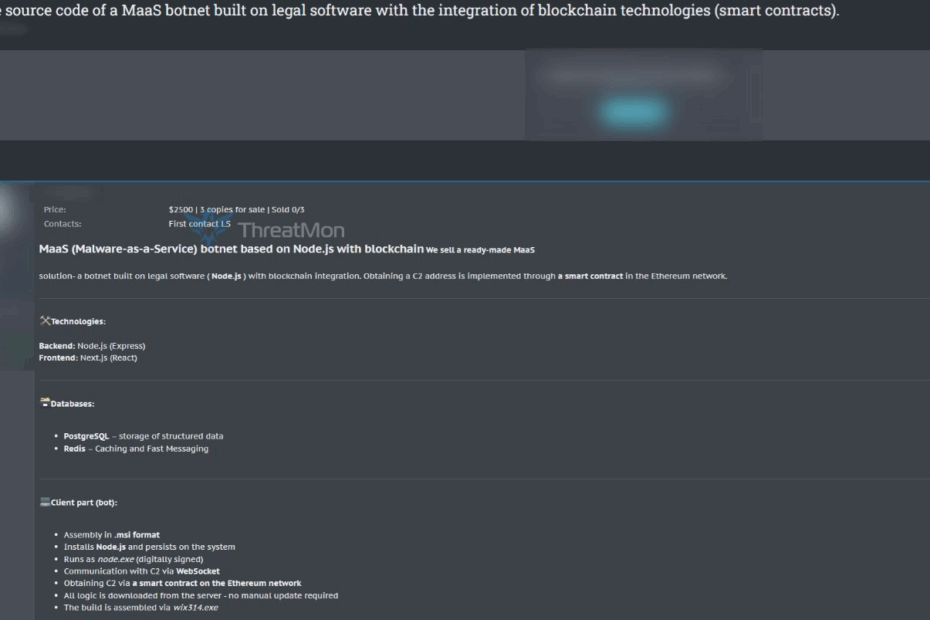
ThreatMon reports that the malware architecture utilizes Node.js as its primary runtime environment, providing cross-platform compatibility and extensive library support for malicious operations.
The framework is further enhanced by Next.js, a React-based web framework that enables the creation of sophisticated command interfaces and administrative dashboards for botnet operators.
The infrastructure backbone relies on PostgreSQL for robust data management and Redis for high-performance caching and session management.
This enterprise-grade database combination allows threat actors to efficiently manage large-scale botnet operations, store victim information, and coordinate distributed attacks across thousands of compromised machines.
The use of these legitimate technologies makes detection significantly more challenging, as security tools must differentiate between malicious usage and legitimate business applications running similar technology stacks.
Most notably, the botnet implements blockchain-based command and control (C2) address acquisition through Ethereum smart contracts.
This innovative approach represents a paradigm shift in botnet communication protocols, as traditional C2 infrastructures rely on centralized servers that can be identified and disrupted by law enforcement.
By leveraging Ethereum’s decentralized network, the botnet can dynamically acquire new C2 addresses through smart contract interactions, making takedown operations exponentially more difficult.
The malware package is distributed as a Microsoft Installer (.msi) file, exploiting Windows’ built-in installation framework to appear legitimate during initial system compromise.
This distribution method leverages social engineering tactics and often masquerades as legitimate software updates or productivity applications.
Once executed, the installer automatically provisions a complete Node.js runtime environment on the victim’s machine, establishing the necessary infrastructure for ongoing malicious operations.
The persistence mechanisms demonstrate advanced evasion techniques, with the malware implementing multiple redundant methods to maintain long-term access to compromised systems.
The WebSocket protocol serves as the primary communication channel between infected machines and the C2 infrastructure, providing real-time bidirectional communication capabilities while appearing as legitimate web traffic to network monitoring systems.
The botnet’s feature set encompasses a comprehensive range of malicious capabilities designed for both intelligence gathering and destructive operations.
Screen capture functionality enables threat actors to conduct espionage activities, capturing sensitive information displayed on victims’ monitors including passwords, financial data, and confidential documents.
The remote code execution (RCE) capability provides attackers with complete administrative control over compromised systems, allowing for privilege escalation, lateral movement, and deployment of additional malicious payloads.
File manipulation capabilities enable comprehensive data exfiltration and system modification operations.
Threat actors can remotely access, modify, delete, or steal files from infected systems, potentially leading to significant data breaches and intellectual property theft.
The combination of these capabilities with the botnet’s stealth-focused design creates a particularly dangerous threat landscape for both individual users and enterprise environments.
The emergence of this MaaS offering on underground forums represents a democratization of advanced cyber attack capabilities, potentially enabling less sophisticated threat actors to conduct operations previously reserved for nation-state actors and advanced persistent threat groups.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post Threat Actors Allegedly Selling MaaS Botnet on Hackers Forums appeared first on Cyber Security News.
“}]]
Read More Cyber Security News