[[{“value”:”
A severe security vulnerability has been discovered in the Acer Control Center software, which could allow attackers to execute arbitrary code with system-level privileges.
The vulnerability, identified in the ACCSvc.exe process, involves misconfigured Windows Named Pipe permissions that enable unauthenticated remote users to exploit the service’s features.
Security researcher Leon Jacobs from Orange Cyber Defense reported this critical flaw, which has been addressed in the latest software update released by Acer on May 15, 2025.
Acer Control Center Vulnerability
The vulnerability stems from improper security configurations in the Windows Named Pipe implementation within the Acer Control Center Service (ACCSvc.exe).
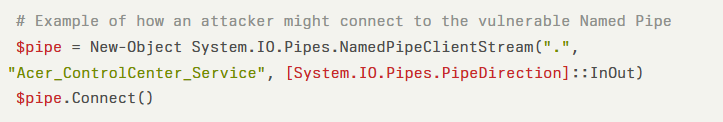
Windows Named Pipes are a mechanism for inter-process communication, allowing processes to exchange data. In this case, the service exposes a Named Pipe using a custom protocol designed to invoke internal functions.
However, the permissions on this pipe were incorrectly configured, allowing any user, including remote unauthenticated attackers, to interact with it.
The most concerning aspect of this vulnerability is that one of the service’s features allows for the execution of arbitrary executables with NT AUTHORITYSYSTEM privileges—the highest level of access in Windows operating systems.
This effectively creates a direct path for privilege escalation, as attackers can leverage this feature to run any code with complete system access.
The exploitation of this vulnerability requires minimal technical expertise. An attacker could craft a simple script to connect to the Named Pipe and issue commands that invoke malicious executables.
Since the service runs with SYSTEM privileges, any code executed through this vulnerability would inherit these elevated permissions. Potential attack scenarios include:
- Installation of persistent backdoors in the system.
- Deployment of ransomware with system-level access.
- Theft of sensitive user data and credentials.
- Complete compromise of the affected machine.
This vulnerability is particularly dangerous in enterprise environments where Acer devices are deployed at scale, as it could facilitate lateral movement across networks and lead to widespread compromise.
Organizations utilizing Acer Control Center in their fleet of devices face significant risk if systems remain unpatched.
Mitigation Steps
Acer has responded to this security issue by releasing an updated version of the Acer Control Center software.
The new version implements proper access controls on the Named Pipe, preventing unauthorized users from interacting with the service’s privileged functions.
Users and system administrators should immediately:
- Download and install the latest Acer Control Center update from the official Acer Drivers and Manuals site.
- Consider implementing network-level controls to restrict access to potentially vulnerable systems until updates can be applied.
For organizations unable to update immediately, temporarily disabling the Acer Control Center Service can serve as a stopgap measure, though this will remove functionality provided by the software.
Live Credential Theft Attack Unmask & Instant Defense – Free Webinar
The post Acer Control Center Vulnerability Let Attackers Execute Malicious Code as a Privileged User appeared first on Cyber Security News.
“}]]
Read More Cyber Security News