[[{“value”:”
Despite sustained international pressure, sanctions, and public exposures over the past two years, the sophisticated Predator mobile spyware has demonstrated remarkable resilience, continuing to evolve and adapt its infrastructure to evade detection while maintaining operations across multiple continents.
The mercenary spyware, originally developed by Cytrox and now operated under the Intellexa alliance, has been active since at least 2019 and represents one of the most persistent threats in the commercial surveillance landscape.
Predator’s attack methodology encompasses both “1-click” and “zero-click” vectors, making it particularly dangerous for high-value targets including politicians, corporate executives, and civil society activists.
The 1-click attacks rely on sophisticated social engineering messages containing malicious links that require minimal user interaction, while zero-click attacks utilize network injection or proximity-based methods that require no action from the target.
Once successfully deployed, Predator provides complete access to a device’s microphone, camera, and all stored data including contacts, messages, photos, and videos, operating without the victim’s awareness.
Recorded Future analysts recently identified a significant resurgence in Predator-related activity, revealing new infrastructure that indicates continued operations despite the implementation of US government sanctions targeting the Intellexa Consortium.
The research uncovered evidence of active operations in over a dozen countries, with more than half of identified customers located in Africa, and revealed a previously unreported presence in Mozambique.
The spyware’s modular Python-based design enables operators to introduce new features remotely without requiring device re-exploitation, making it exceptionally persistent and adaptable.
.webp)
This flexibility has allowed Predator to maintain effectiveness even as security researchers and technology companies have worked to identify and mitigate entire classes of vulnerabilities that mercenary spyware typically exploits.
The deployment patterns observed by researchers indicate that Predator’s expensive licensing model reserves its use for strategic, high-value targets, with documented cases of abuse primarily targeting civil society actors, journalists, activists, and political figures.
The cross-border targeting capabilities have been particularly concerning, with instances documented where operators linked to one country have successfully targeted officials and parliamentarians in other nations.
Multi-Tiered Infrastructure Evolution and Detection Evasion
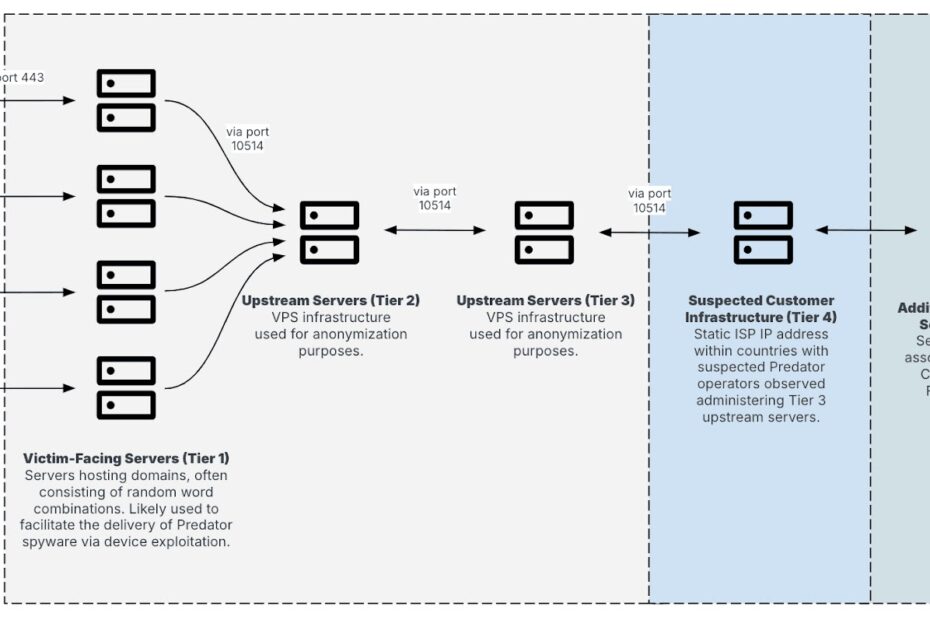
The most significant development in Predator’s operational sophistication lies in its expanded multi-tiered infrastructure network, which has evolved from a three-layer system to a more complex four-tier architecture designed to further obscure the identification of countries deploying the spyware.
This enhanced infrastructure closely resembles the high-level architecture outlined in previous security research but demonstrates continuous evolution in response to public exposure and security enhancements.
The current infrastructure operates through distinct communication layers, with Tier 1 servers consistently communicating with dedicated Tier 2 upstream virtual private server IP addresses using Transmission Control Protocol port 10514.
These upstream servers function as anonymization hop points, making direct association between Tier 1 servers and individual Predator customers significantly more difficult to establish.
The communication pattern continues through Tier 2 to Tier 3 servers using the same TCP port 10514, with Tier 3 servers subsequently relaying traffic to Tier 4 infrastructure corresponding to static, in-country Internet Service Provider IP addresses suspected to be under Predator customer control.
.webp)
A notable addition to this infrastructure is the tracking of a fifth layer, designated as Tier 5, which appears to play a central role in Predator-related operations and has been linked to a Czech entity, FoxITech s.r.o., previously associated with Intellexa.
This additional layer represents a significant expansion in operational complexity, suggesting increased investment in infrastructure obfuscation capabilities.
The operators have also implemented sophisticated detection evasion strategies, including the deployment of fake websites that fall into four main categories: counterfeit 404 error pages, fraudulent login or registration pages, sites indicating construction status, and websites purporting association with legitimate entities such as conferences.
These deception tactics, combined with the expanded use of varied server configurations across previously unused Autonomous System Numbers, demonstrate the operators’ commitment to maintaining operational security despite increased scrutiny from security researchers and law enforcement agencies.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full acces
The post Predator Mobile Spyware Remains Consistent with New Design Changes to Evade Detection appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News