[[{“value”:”
The cryptocurrency and blockchain development ecosystem is facing an unprecedented surge in sophisticated malware campaigns targeting the open source supply chain.
Over the past year, threat actors have significantly escalated their attacks against Web3 developers by publishing malicious packages to trusted registries including npm and PyPI, exploiting the implicit trust developers place in these repositories.
These campaigns represent a calculated shift toward financially motivated attacks that leverage the unique vulnerabilities present in blockchain development environments.
The attack landscape has become increasingly concentrated, with approximately 75% of malicious blockchain-related packages hosted on npm, 20% on PyPI, and the remainder distributed across registries such as RubyGems and Go Modules.
While Ethereum and Solana continue to be the primary targets, recent campaigns have expanded to include TRON and TON platforms, indicating growing threat actor interest in a wider range of wallet formats and alternative layer-1 blockchain ecosystems.
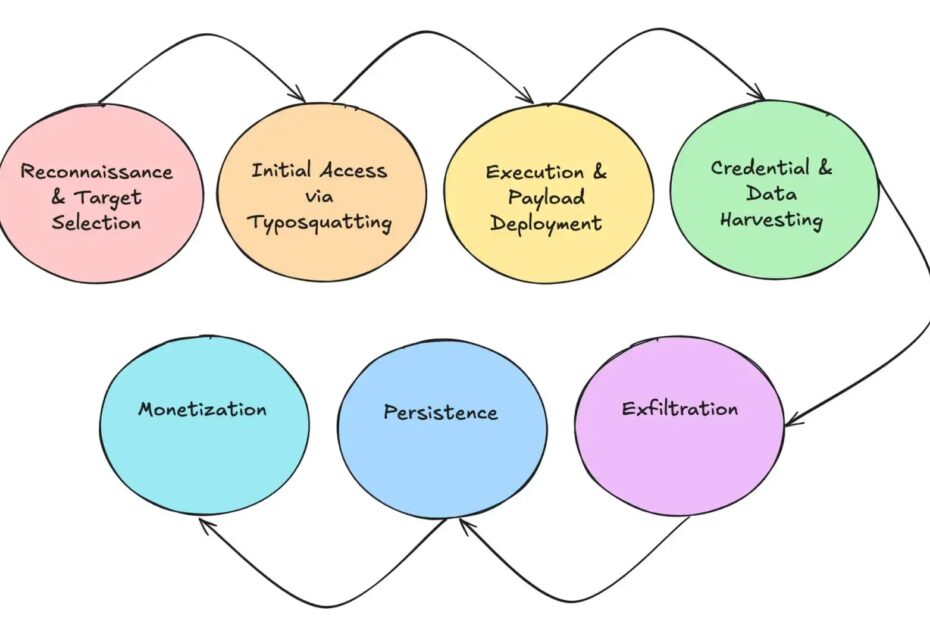
Socket.dev analysts identified four recurring threat classes that dominate the current landscape: credential stealers, crypto drainers, cryptojackers, and clipboard hijackers.
These malicious packages exploit the unique attack surface created by blockchain developers’ reliance on open source dependencies, combined with CI/CD pipelines that often lack strict dependency validation or isolation.
The threat actors leverage package lifecycle hooks such as postinstall in npm and setup.py in PyPI to trigger malicious behavior immediately upon installation, even when packages are never imported or actively used.
The financial impact of these attacks has been severe, with threat actors successfully extracting millions in cryptocurrency from compromised development environments.
The malware campaigns demonstrate sophisticated understanding of Web3 development workflows, targeting specific wallet paths, browser extensions, and development tools commonly used by blockchain developers.
Advanced Credential Theft Mechanisms
The most sophisticated aspect of these supply chain attacks lies in their credential extraction capabilities, which have evolved far beyond simple file system scraping.
.webp)
Modern credential stealers employ multi-layered approaches that combine direct file system access with runtime manipulation to capture sensitive cryptographic material from developer environments.
Advanced stealers implement monkey-patching techniques that intercept keypair generation at the library level without modifying source files.
In documented PyPI campaigns, malware intercepted Solana keypair creation by modifying library methods at runtime, capturing private keys during generation, encrypting them with hardcoded RSA-2048 public keys, and embedding the encrypted data in blockchain memo transactions sent to Solana Devnet.
.webp)
This technique allows threat actors to retrieve and decrypt stolen credentials remotely while maintaining stealth.
// Example of typical credential stealer targeting common wallet paths
const fs = require('fs');
const path = require('path');
const walletPaths = [
'~/.config/solana/id.json',
'~/.ledger-live',
'~/Library/Application Support/Exodus/exodus. Wallet'
];
walletPaths.forEach(walletPath => {
if (fs.existsSync(path.expanduser(walletPath))) {
// Exfiltrate wallet data via encrypted channels
}
});Nation-state actors, particularly those linked to North Korea’s Contagious Interview campaign, have weaponized trusted developer tools including linters, validators, and post-processing libraries to deliver credential stealers and backdoors.
These attacks bypass traditional security measures including multi-factor authentication and hardware wallets by compromising the development environment itself, establishing persistence through scheduled tasks and startup entries to ensure recurring access to victim systems.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post Threat Actors Attacking Cryptocurrency and Blockchain Developers with Weaponized npm and PyPI Packages appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News