[[{“value”:”
A security researcher has published a detailed analysis demonstrating how Kernel Address Space Layout Randomization (KASLR) protections can be circumvented on Windows 11 24H2 systems through exploitation of an HVCI-compatible driver with physical memory access capabilities.
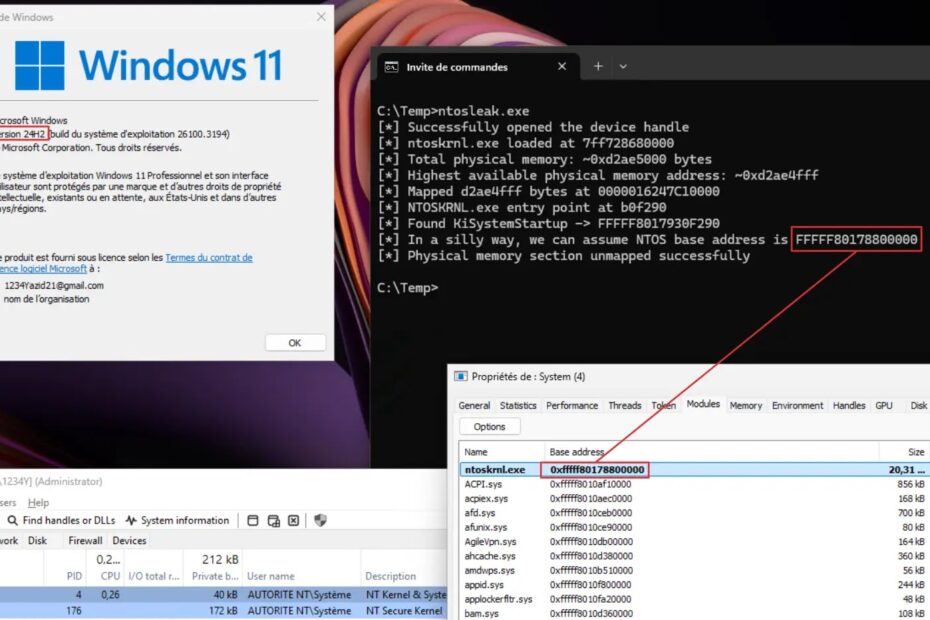
The research, published by security researcher Yazid on June 9, 2025, presents a novel approach to obtaining the Windows kernel base address by leveraging the eneio64.sys driver, which provides read and write primitives on the system’s physical memory.
The demonstration represents a continuation of previous research into exploiting HVCI-compatible kernel drivers, specifically focusing on how attackers or security researchers can simulate the translation of physical addresses into virtual addresses using paging structures.
This technique becomes particularly relevant given Microsoft’s recent security enhancements in Windows 11 24H2, which now require SeDebugPrivilege for operations that previously worked from medium integrity processes, such as using EnumDeviceDrivers or NtQuerySystemInformation to leak kernel module addresses.
Xacone researchers noted that traditional KASLR bypass methods have become increasingly challenging on modern Windows systems, with tools like prefetch-tool showing inconsistent results across different environments.
The researcher specifically mentions that while such tools worked on host machines, they failed to function reliably on Windows 11 24H2 virtual machine environments used for testing.
The technique exploits the Low Stub, a data structure consistently present at the beginning of physical memory layouts on HVCI-enabled systems, located between physical addresses 0x10000 and 0x20000.
This structure contains various kernel addresses, including those of non-exported functions, though many are specific to the Hardware Abstraction Layer (HAL).
Technical Implementation and Memory Scanning Methodology
The core innovation of this research lies in its approach to identifying the kernel’s entry point within the Low Stub structure.
Rather than relying on hardcoded offsets or traditional enumeration methods, the technique searches for the KiSystemStartup function address, which serves as the kernel’s entry point.
The researcher demonstrates how to parse the PE image of ntoskrnl.exe to retrieve the Relative Virtual Address (RVA) of the entry point, then scan the Low Stub for addresses matching the last three bytes of this RVA.
.webp)
The implementation involves a systematic memory scan using the following approach: for (physical_offset = 0x10000; physical_offset < 0x20000; physical_offset += 8) to iterate through potential Low Stub locations, reading 64-bit values and comparing them against the known entry point pattern.
When a match is found using the condition if ((qword_value & 0xFFFFF) == (ntosEntryPoint & 0xFFFFF)), the kernel base address can be calculated by subtracting the entry point’s RVA from the discovered address.
The Windows kernel’s alignment to 2MB boundaries, leveraging large-page memory mappings, ensures consistent address patterns that facilitate this detection method across different system configurations.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post Windows 11 24H2 KASLR Broken Using an HVCI-Compatible Driver with Physical Memory Access appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News