[[{“value”:”
A sophisticated network of 71 fraudulent websites impersonating a major German discount retailer has been uncovered, revealing an elaborate scheme designed to steal payment information and personal data from unsuspecting consumers.
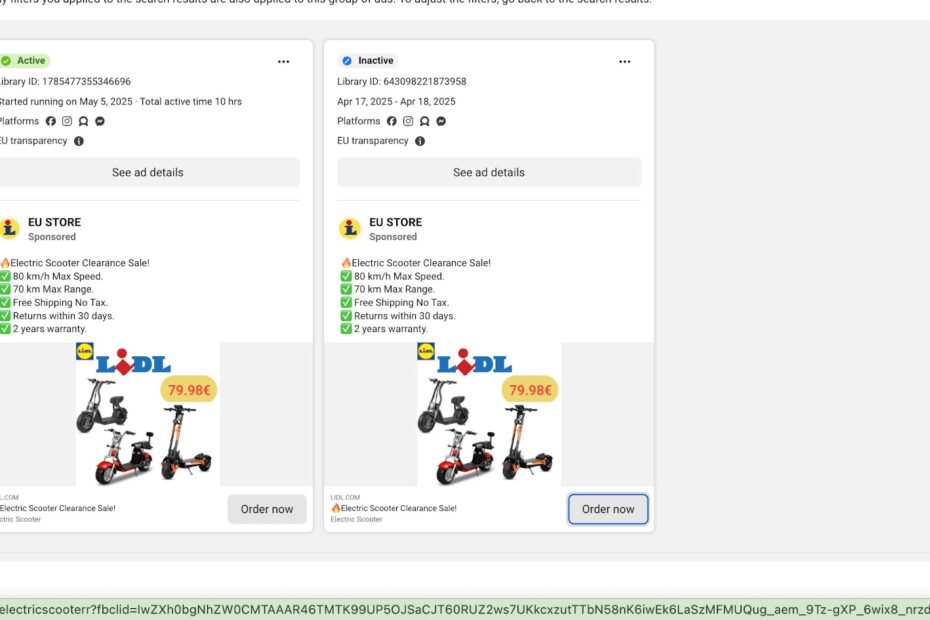
These sites employ typosquatting techniques, using domain names that closely mimic legitimate retailer addresses, while simultaneously running deceptive online ad campaigns to lure victims.
The operation has been active since at least February 2025, primarily targeting European consumers with fraudulent discount offers for electronics and household goods.
The scam’s architecture differs from typical phishing operations in that these fake websites don’t merely collect data—they actively process payments through compromised merchant accounts.
Victims who believe they’re purchasing heavily discounted electric scooters and other products from a trusted retailer are instead sending their payment details directly to fraudsters, who capture the financial information while never delivering any merchandise.
The scheme represents a growing trend in e-commerce fraud that combines brand impersonation with functional payment processing capabilities.
Recorded Future Payment Fraud Intelligence researchers identified the network after spotting lidlorg[.]com on April 19, 2025, a site designed to impersonate Lidl, the German international discount retailer chain.
Through subsequent investigation, analysts linked this initial discovery to a broader network of 71 domains using similar tactics and shared merchant infrastructure.
“This campaign demonstrates a concerning evolution in purchase scams,” noted the Recorded Future team in their analysis.
“The operators have created an entire ecosystem of fake storefronts, advertisement networks, and payment processing channels to maximize their ability to defraud consumers and harvest financial data for downstream fraud.”
At the core of this operation is a sophisticated infrastructure connecting seemingly disparate websites through twelve shared merchant accounts.
These accounts, with names like AKRU KERAMIK GMBH, MYCOZYBABIES, and YSPCLOTHINGGSHOP, process victim payments while enabling the theft of personal and financial information.
The domains themselves exhibit common characteristics, having been operational for approximately 65 days on average and scoring an alarming 88/100 on DomainTools risk assessment metrics.
Anatomy of the Scam Network
The technical infrastructure behind this fraud operation reveals meticulous planning and coordination.
.webp)
The attackers leverage Facebook ad accounts with names like “EU STORE” and “L Clearance” to distribute advertisements featuring the impersonated retailer’s logo alongside too-good-to-be-true offers.
These advertisements direct victims to the network of fake domains, which are engineered to look legitimate while concealing their malicious purpose.
What makes this scam network particularly notable is its payment processing capability. Unlike traditional phishing sites that merely collect information, these domains complete the fraud cycle by processing actual transactions through compromised merchant accounts.
The merchant accounts associated with the domains show clear signs of transaction laundering—the practice of disguising high-risk or fraudulent transactions as legitimate business.
For instance, PETHOUSEN LLC officially lists its URL as pethousen[.]com, but Recorded Future researchers discovered it processing payments for scam domains biliability[.]com, dknyonlineuk[.]com, and outletmalleu[.]shop.
The investigation has yet to determine whether this network is operated by a single sophisticated threat actor or represents a collaborative effort among multiple criminal entities sharing resources.
The merchant infrastructure could be part of a “cash-out” service being rented on dark web markets, or the entire operation might be controlled by a single group rotating domain and merchant combinations to evade detection.
Financial institutions are advised to block transactions with the identified merchant accounts and monitor any customer cards that have previously transacted with them for additional fraud signals. Merchant acquirers should analyze similar merchant registrations in their portfolios to identify other potentially compromised accounts.
With the operation continuing to deploy new domains and advertising campaigns as old ones are detected and taken down, vigilance remains essential for both consumers and financial institutions in identifying and avoiding these increasingly sophisticated purchase scams.
Equip your SOC team with deep threat analysis for faster response -> Get Extra ������� �������� for Free
The post 71 Fake Sites Using Brand Scam to Steal Payment Info Linked to German Retailer appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News