[[{“value”:”
Security researcher Sean has successfully identified a zero-day vulnerability in the Linux kernel using OpenAI’s o3 model. The discovery, designated as CVE-2025-37899, represents a significant milestone in AI-assisted vulnerability research.
The vulnerability, officially confirmed on May 20, 2025, affects the ksmbd component of the Linux kernel – an in-kernel server that implements the SMB3 protocol for sharing files over networks.
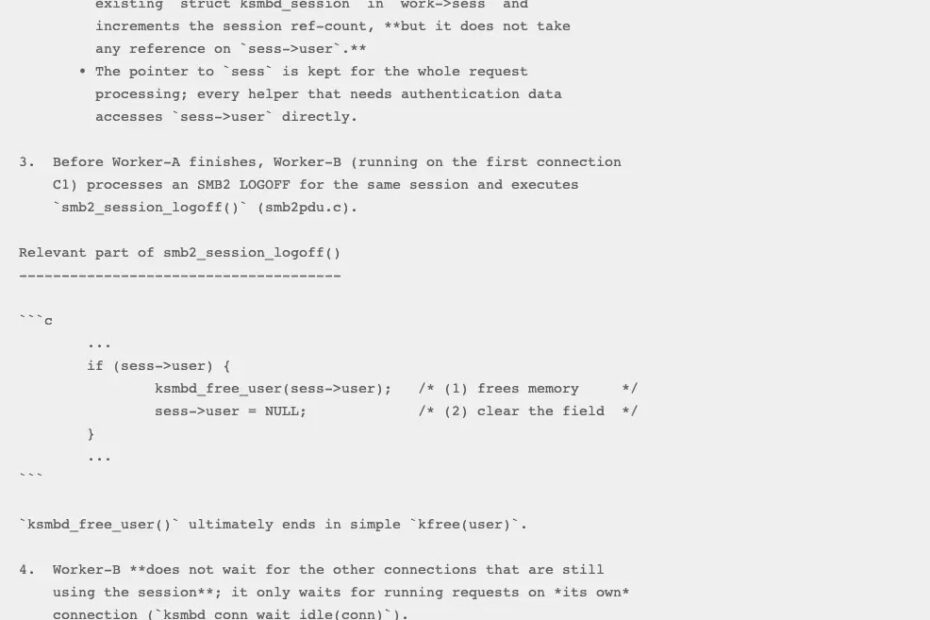
Specifically, a use-after-free vulnerability in the handler for the SMB ‘logoff’ command was identified that could potentially lead to serious security breaches.
“I found the vulnerability with nothing more complicated than the o3 API – no scaffolding, no agentic frameworks, no tool use,” stated Sean, who discovered the flaw. “This is, as far as I’m aware, the first public discussion of a vulnerability of that nature being found by a large language model, Sean said.
The technical details reveal that when one thread is processing a logoff command, it frees the sess->user object.
However, suppose another connection has sent a session setup request to bind to the session being freed. In that case, the handler for that connection could simultaneously be accessing sess->user, resulting in a classic use-after-free scenario.
Such vulnerabilities can lead to memory corruption and potentially allow attackers to execute arbitrary code with kernel privileges.
OpenAI’s o3 model, released on April 16, 2025, represents a significant advancement in AI reasoning capabilities. The model is designed to “think for longer before responding” and demonstrates substantially improved performance in complex tasks, including coding and mathematics.

Its ability to understand complex code structures and reason about concurrent operations proved crucial in identifying this vulnerability.
“With o3, LLMs have made a leap forward in their ability to reason about code, and if you work in vulnerability research, you should start paying close attention,” Sean noted. “They are now at a stage where they can make you significantly more efficient and effective.”
Security experts rate this vulnerability with a high severity score, though the Exploit Prediction Scoring System (EPSS) currently estimates a relatively low exploitation probability of 0.02%. The vulnerability affects multiple Linux kernel versions up through 6.12.27, 6.14.5, and 6.15-rc4.
Linux distributions, including SUSE, are already working on patches. The SUSE Security Team currently rates the issue as having “moderate severity.” Users are encouraged to apply updates as they become available.
The discovery marks a watershed moment in how AI systems might transform security research. Rather than replacing human security researchers, models like o3 are proving to be powerful assistants that can efficiently analyze complex codebases.
“If you’re an expert-level vulnerability researcher or exploit developer, the machines aren’t about to replace you,” Sean emphasized. “In fact, it is quite the opposite: they are now at a stage where they can make you significantly more efficient and effective.”
As AI models continue to evolve, this discovery suggests a future where human-AI collaboration becomes standard practice in identifying and mitigating critical security vulnerabilities before malicious actors can exploit them.
Find this News Interesting! Follow us on Google News, LinkedIn, & X to Get Instant Updates!
The post Linux kernel SMB 0-Day Vulnerability Uncovered Using ChatGPT appeared first on Cyber Security News.
“}]]
Read More  Cyber Security News
Cyber Security News