[[{“value”:”
A sophisticated cryptojacking campaign has emerged targeting widely-used DevOps applications through the exploitation of common misconfigurations rather than zero-day vulnerabilities.
The campaign, which has been observed targeting HashiCorp Nomad, Consul, Docker API, and Gitea deployments, represents a significant shift in how threat actors are approaching infrastructure compromise in cloud environments.
The attack campaign demonstrates a calculated approach to resource theft, with threat actors focusing on publicly accessible DevOps web servers that have been deployed without proper security configurations.
Unlike traditional malware campaigns that rely on custom payloads or attacker-controlled infrastructure, this operation employs a “living-off-open-source” methodology, downloading legitimate tools directly from public repositories to avoid detection mechanisms that typically flag suspicious binaries or command-and-control communications.
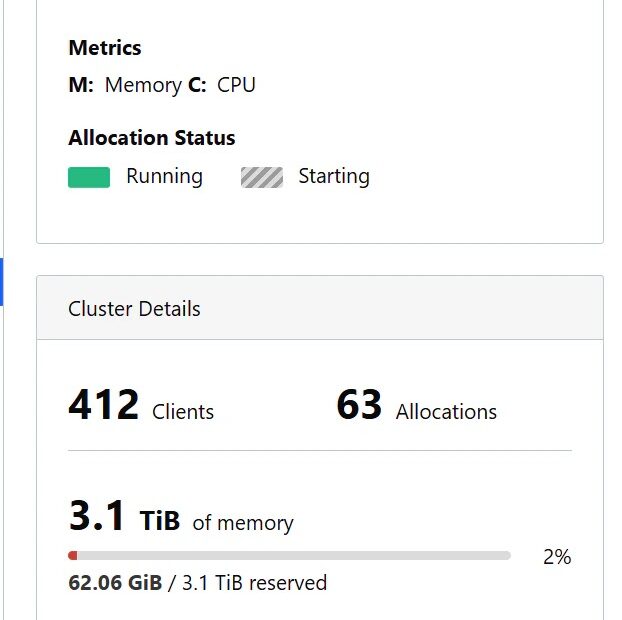
Wiz analysts identified the threat actor behind these activities, designated as JINX-0132, while investigating anomalous behavior across multiple DevOps platforms.
The researchers noted that this campaign marks what they believe to be the first publicly documented instance of Nomad misconfigurations being exploited as an attack vector in the wild.
The discovery underscores how misconfiguration abuse can often evade traditional security monitoring, particularly when targeting applications that are not commonly recognized as high-risk attack vectors.
.webp)
The scale of the campaign is particularly concerning, with some compromised instances managing hundreds of clients with combined computational resources worth tens of thousands of dollars per month.
This highlights how even well-funded organizations with substantial security budgets remain vulnerable to fundamental configuration errors.
According to Wiz data, approximately 25% of all cloud environments contain at least one of the targeted technologies, with 5% of these deployments exposed directly to the Internet, and alarmingly, 30% of those exposed instances are misconfigured.
The threat actor’s methodology deliberately avoids traditional indicators of compromise, instead relying on standard release versions of legitimate mining software and public repositories for payload delivery.
This approach significantly complicates attribution efforts and makes clustering the actor’s activities more challenging for security teams attempting to track the campaign’s full scope.
Nomad Exploitation Mechanism
The exploitation of HashiCorp Nomad represents the most technically sophisticated aspect of the JINX-0132 campaign.
Nomad, a scheduler and orchestrator for deploying applications across multiple platforms, is explicitly documented as not being secure-by-default, requiring administrators to implement proper security configurations.
.webp)
The fundamental vulnerability lies in Nomad’s job queue functionality, which allows any user with access to the server API to create and execute tasks on registered nodes.
When JINX-0132 gains access to a misconfigured Nomad deployment, they create multiple malicious jobs with seemingly random names like “resitajt” and “mbuvvcwm”.
Each job contains a task configuration that downloads XMRig mining software directly from its official GitHub repository.
The attack payload executes a series of commands that update the system, install wget, download the XMRig archive, extract it, set execution permissions, and launch the miner connecting to the pool.supportxmr.com mining pool using the attacker’s wallet address.
The task configuration demonstrates the actor’s preference for redundancy, attempting both regular and sudo-elevated commands to ensure successful execution regardless of the compromised system’s privilege structure.
The mining operation is configured to utilize up to 90% of available CPU threads, maximizing resource extraction while maintaining system stability to avoid detection through performance degradation.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post Threat Actors Exploiting DevOps Web Servers Misconfigurations To Deploy Malware appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News