[[{“value”:”
Cybersecurity researchers have identified a sophisticated new remote access trojan called DuplexSpy RAT that enables attackers to establish comprehensive surveillance and control over Windows systems.
This multifunctional malware represents a growing trend in modular, GUI-driven threats that significantly lower the technical barrier for cybercriminals seeking to compromise target machines.
The malware, developed in C# with a clean graphical interface and configurable options, allows operators to tailor attacks with minimal coding knowledge while maintaining deep integration with Windows internals.
DuplexSpy RAT employs advanced encryption techniques, utilizing both AES-256-CBC and RSA-4096 algorithms to secure communications between infected hosts and command-and-control servers, effectively evading network detection mechanisms.
.webp)
CYFIRMA analysts identified that the tool was released publicly on GitHub by developer ISSAC/iss4cf0ng, ostensibly for “educational purposes,” though its versatility and ease of customization make it highly attractive for malicious use by threat actors.
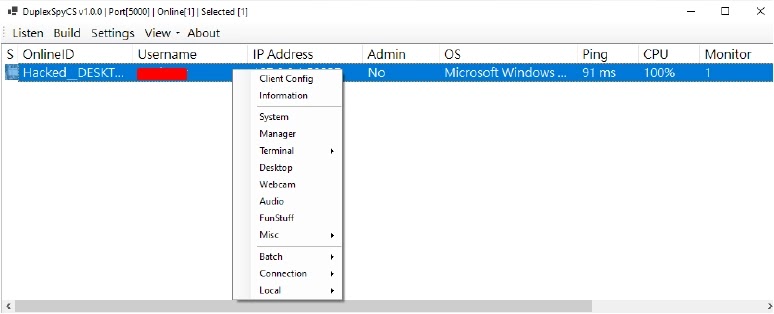
The RAT’s design reflects a sophisticated understanding of both offensive tooling and Windows architecture, enabling attackers to establish persistent backdoors while mimicking legitimate system processes to avoid detection.
The malware’s impact extends far beyond traditional remote access capabilities, incorporating comprehensive surveillance features including keystroke logging, real-time screen capture, webcam and microphone monitoring, and interactive command shell access.
.webp)
These capabilities transform compromised systems into comprehensive surveillance platforms, allowing attackers to monitor user activities, capture sensitive information, and maintain long-term access to target environments.
Sophisticated Persistence and Stealth Mechanisms
DuplexSpy RAT employs a multi-layered persistence strategy that ensures survival across system reboots and potential cleaning attempts.
The malware implements a dual-pronged approach, copying itself to the user’s startup folder under the deceptive name “Windows Update.exe” while simultaneously creating corresponding registry entries.
The persistence mechanism begins during initialization, where the malware executes sophisticated installer routines. The code demonstrates this approach:-
installer.m_szStartUpName = Environment.ExpandEnvironmentVariables(Path.Combine(Environment.GetFolderPath(Environment.SpecialFolder.Startup), _szCopyStartup));
installer.m_bReg = _bReg;
installer.m_szRegKeyName = m_szRegKeyName;This installation process places the malware in the Windows startup directory at “C:UsersAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup” while creating a registry entry under “HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun” with the key name “Windows Update”.
This dual persistence ensures automatic execution upon system boot through multiple vectors.
.webp)
The malware further enhances its stealth profile by implementing sophisticated anti-analysis capabilities.
It actively monitors system processes at 100-millisecond intervals, targeting security tools and analysis applications.
When security software is detected, DuplexSpy terminates these processes while displaying deceptive error messages referencing corrupted system files like “user32.dll” to mislead users and prevent investigation.
Additionally, the RAT employs fileless execution techniques, loading itself directly into memory and subsequently deleting the original executable from disk.
This approach leaves minimal forensic traces, as demonstrated in the LoadToMemory() method that reads the executable into memory, creates execution threads, and triggers self-destruction routines.
The malware’s ability to operate entirely in memory while maintaining persistence through registry modifications and startup folder placement represents a sophisticated evasion strategy that challenges traditional detection methods.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post New DuplexSpy RAT Let Attackers Gain Complete Control of Windows Machine appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News