[[{“value”:”
Security researchers have uncovered an active cyberattack campaign targeting Langflow servers through CVE-2025-3248, a critical remote code execution vulnerability that allows threat actors to deploy the sophisticated Flodrix botnet malware.
The attacks demonstrate how cybercriminals are rapidly weaponizing newly disclosed vulnerabilities to compromise cloud infrastructure and expand their botnet operations.
CVE-2025-3248, rated with a CVSS score of 9.8, affects Langflow versions prior to 1.3.0 and has been added to CISA’s Known Exploited Vulnerabilities catalog.
The vulnerability resides in the /api/v1/validate/code endpoint, which fails to implement adequate authentication while processing user-supplied Python code snippets.
Attackers can exploit this flaw by sending crafted POST requests containing malicious Python payloads embedded within function default arguments or decorators.
The vulnerability allows remote attackers to achieve code execution without authentication, as Langflow processes the malicious code by parsing it into an Abstract Syntax Tree using ast.parse(), then compiling and executing it via Python’s compile() and exec() functions. This design flaw enables complete system compromise on affected servers.
Langflow RCE Vulnerability Exploited
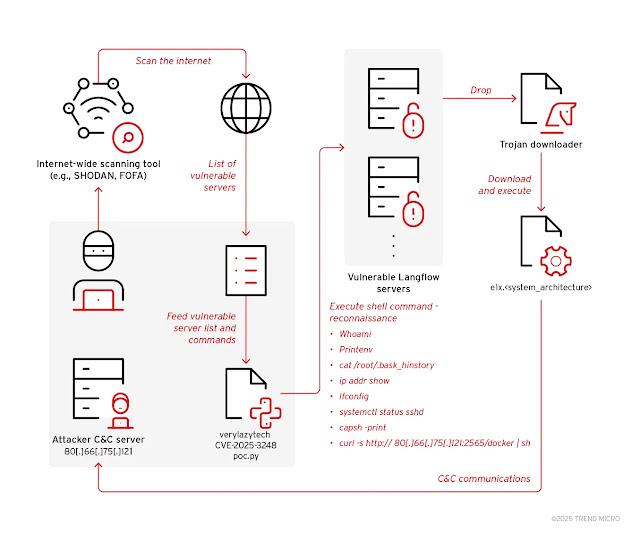
Cybercriminals have developed a systematic approach to exploit vulnerable Langflow installations. They begin by scanning the internet using tools like Shodan or FOFA to identify publicly exposed Langflow servers. Once targets are identified, attackers utilize an open-source proof-of-concept exploit from GitHub to gain remote shell access on vulnerable systems.
Following initial compromise, the attackers execute various reconnaissance commands, including whoami, printenv, cat /root/.bash_history, ip addr show, and systemctl status sshd to gather system information.
The collected intelligence is transmitted back to command-and-control servers, likely for identifying high-value targets for further exploitation.

The attack culminates with the deployment of a Trojan downloader script named “docker” that fetches and executes the Flodrix botnet payload from attacker-controlled infrastructure at IP address 80.66.75.1211. The malware downloader attempts to install architecture-specific variants of the botnet across multiple system types.
The Flodrix botnet represents an evolution of the LeetHozer malware family, incorporating advanced stealth techniques, including self-deletion and artifact removal, to evade detection. The malware employs string obfuscation using XOR encryption with the key “qE6MGAbI” to conceal command-and-control server addresses.
Once installed, Flodrix establishes dual communication channels with its infrastructure using both TCP and UDP protocols. The botnet can execute various distributed denial-of-service attacks including tcpraw, udpplain, handshake, tcplegit, ts3, and udp attack types based on commands received from the control servers.
Additionally, the malware actively terminates competing processes and sends detailed system information to operators via UDP notifications.
Organizations running Langflow must immediately upgrade to version 1.3.0 or later, which implements proper authentication requirements for the vulnerable endpoint. The patch adds a _current_user: CurrentActiveUser parameter that validates user sessions before permitting access to code validation functionality.
System administrators should also restrict public access to Langflow endpoints, monitor for indicators of compromise, and scan for the presence of hidden files like .system_idle that the malware uses for persistence tracking.
Automate threat response with ANY.RUN’s TI Feeds—Enrich alerts and block malicious IPs across all endpoints -> Request full access
The post Hackers Actively Exploiting Langflow RCE Vulnerability to Deploy Flodrix Botnet appeared first on Cyber Security News.
“}]]
Read More  Cyber Security News
Cyber Security News