[[{“value”:”
A significant surge in sophisticated recruitment scams has emerged, with cybercriminals exploiting economic vulnerabilities and the competitive job market to target desperate job seekers.
These scams employ increasingly refined social engineering tactics that blend legitimate recruitment practices with fraudulent schemes, making them particularly effective at evading detection while extracting money and personal information from victims.
Security researchers have identified three distinct threat actors deploying targeted campaigns against job seekers worldwide.
The first impersonates technology companies using advance fee fraud tactics, the second operates a localized scheme across 18 countries impersonating a logistics recruitment agency, and the third masquerades as the Government of Singapore to harvest national identity numbers and compromise Telegram accounts.
These diverse approaches highlight the evolving nature of recruitment-based cyber threats.
According to Federal Trade Commission data, losses from job-related fraud in the United States exceeded $500 million in 2023, more than doubling the $200 million reported in 2022.
This dramatic increase reflects both the growing sophistication of these scams and the expanding pool of vulnerable targets created by economic pressures, cost-of-living challenges, and the rise of gig work opportunities.
Netcraft researchers identified that these scam operations are carefully structured to maximize persistence and scale while evading detection measures.
Their analysis revealed that operators typically employ multiple personas throughout the scam lifecycle – one to make initial contact and another to execute the fraud – allowing them to efficiently manage high volumes of victims while maintaining operational security when communication channels are disrupted.
The cybercriminals have engineered these schemes to exploit specific vulnerabilities in how job seekers evaluate opportunities, particularly targeting those attracted to flexible working arrangements and above-average compensation packages, which have become increasingly desirable in the post-pandemic economy.
Inside the Celadon and Softserv Scam Operation
The most prolific of the identified threats begins with unsolicited messages via WhatsApp, Telegram or other messaging platforms, with attackers posing as recruitment consultants claiming to have received applications from potential victims.
Initial outreach typically originates from international phone numbers, creating a false impression of legitimacy while making verification more difficult for targets.
After establishing contact, victims are directed to communicate with a second persona who provides job details – typically featuring unrealistically high compensation rates for simple tasks.
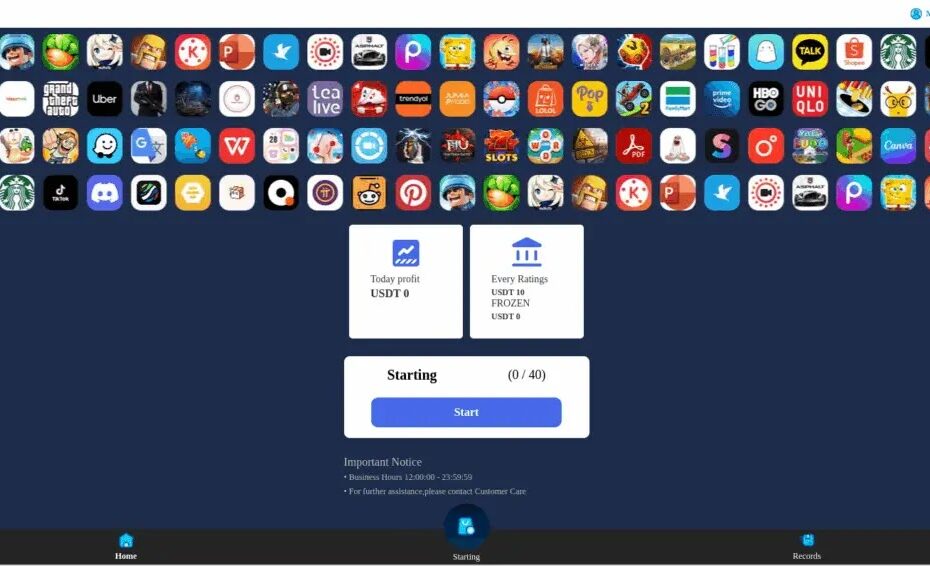
Netcraft analysts documented that the Celadon/Softserv operation offers payment in cryptocurrency (USDT) and requires victims to register on specialized domains like celadonsoftapp[.]vip that feature convincing but fraudulent interfaces.
The infection pathway systematically escalates commitment through a carefully designed user journey. After registration, victims receive nominal “credit” to their accounts before being prompted to deposit actual funds to “activate” various task levels that promise profitable returns.
.webp)
These task interfaces incorporate familiar app icons to enhance perceived legitimacy.
Infrastructure analysis revealed nine similar platform sites operated by this threat actor between May and November 2024, all sharing identical design elements and server infrastructure.
The domains, all protected by Cloudflare and hosted through Gname, demonstrate the operation’s scale and sophisticated approach to persistence.
The threat actor’s detection evasion techniques include requiring registration codes for website access, implementing login barriers to prevent security researcher analysis, and redesigning interfaces periodically to maintain effectiveness.
.webp)
Besides this, it documents their transition to more professional-appearing interfaces in late June 2024, indicating ongoing refinement of their techniques.
Job seekers should remain vigilant for warning signs including communication exclusively through messaging apps, implausibly high compensation offers, cryptocurrency payment methods, and pressure to make upfront deposits.
Are you from the SOC and DFIR Teams? – Analyse Real time Malware Incidents with ANY.RUN -> Start Now for Free.
The post Threat Actors Attacking Job Seekers With Three New Unique Adversaries appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News