[[{“value”:”
Recent cybersecurity research has revealed sophisticated patterns within TCP SYN segments that cybercriminals are exploiting to establish covert communication channels and evade traditional network security measures.
This groundbreaking analysis demonstrates how attackers manipulate fundamental networking protocols to create nearly undetectable malware infrastructure, representing a significant evolution in cyber threat methodologies.
The emergence of this TCP SYN-based malicious activity represents a paradigm shift in how cybercriminals approach network infiltration and persistence.
.webp)
Unlike conventional malware that relies on application-layer protocols or well-known ports, this sophisticated approach exploits the three-way handshake mechanism fundamental to TCP communications.
The malware leverages subtle variations in SYN packet structures, timing intervals, and sequence number patterns to establish command and control channels that appear as legitimate network traffic to most monitoring systems.
The attack vectors associated with this technique demonstrate remarkable versatility and stealth capabilities.
Initial compromise typically occurs through traditional methods such as phishing emails or software vulnerabilities, but the subsequent communication infrastructure relies entirely on manipulated TCP SYN segments.
The malware embeds control instructions within seemingly normal connection establishment attempts, allowing attackers to maintain persistent access while avoiding detection by conventional deep packet inspection systems.
Netscout analysts identified this emerging threat pattern while conducting routine network traffic analysis across multiple enterprise environments.
Their research uncovered that infected systems generate SYN packets with carefully crafted TCP options fields and non-standard initial sequence numbers that serve as covert data channels.
The impact extends beyond simple data exfiltration, as this technique enables attackers to establish robust botnet infrastructures that can survive network monitoring and security appliance scrutiny.
The broader implications for network security are profound, as this approach fundamentally challenges existing detection methodologies.
Traditional security tools focus on analyzing established connections and payload content, while this malware operates within the connection establishment phase itself.
Enterprise networks experiencing this activity often show normal traffic patterns in their security dashboards, making identification extremely challenging without specialized analysis tools.
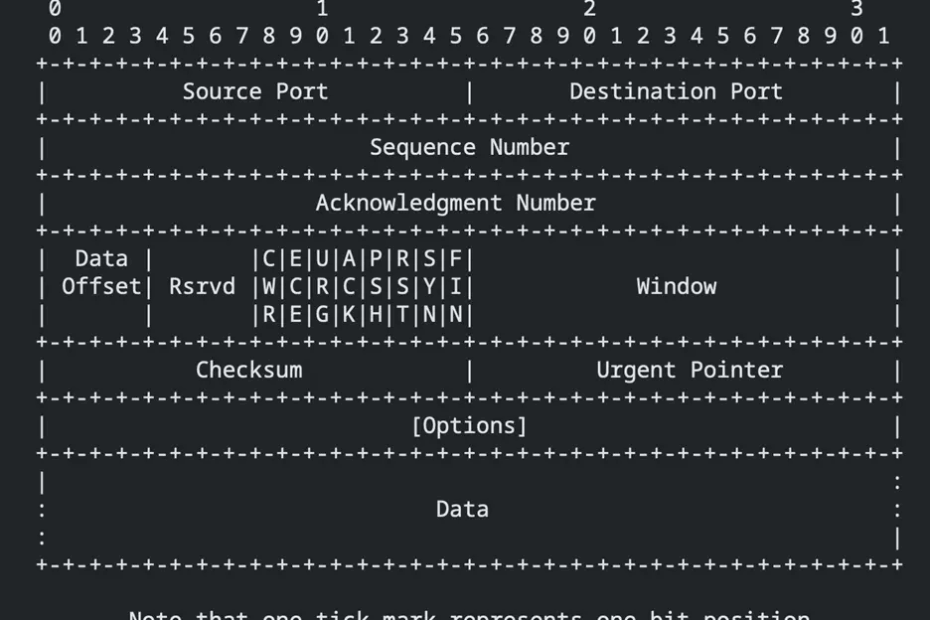
Infection Mechanism and Protocol Manipulation
The core infection mechanism exploits TCP sequence number randomization and option field manipulation to create a bidirectional communication channel.
When establishing outbound connections, infected systems incorporate command responses within the initial sequence number calculation, using a predetermined algorithm that allows remote operators to extract data from connection attempts.
The malware implements a custom encoding scheme that maps control instructions to specific TCP window size values and timestamp options.
def encode_command(data, base_seq):
encoded_seq = base_seq + (hash(data) & 0xFFFF)
tcp_options = [(8, struct.pack('!L', int(data[:8], 16)))]
return encoded_seq, tcp_optionsThis technique proves particularly effective because SYN packets naturally traverse firewalls and security appliances as part of legitimate connection establishment processes.
Try in-depth sandbox malware analysis for your SOC team. Get ANY.RUN special offer only until May 31 -> Try Here
The post New Research Uncovers Critical Patterns in TCP SYN Segments to Capture Malicious Activity appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News