[[{“value”:”
Operant AI has launched Woodpecker, an open-source automated red teaming engine designed to democratize advanced security testing across AI systems, Kubernetes environments, and APIs.
The tool addresses the growing complexity of security vulnerabilities as organizations increasingly adopt cloud-native applications and artificial intelligence technologies.
Woodpecker already simulates more than 50% of OWASP Top 10 threats across APIs, Kubernetes, and Large Language Models (LLMs), exceeding the threat simulation scope of leading commercial red teaming products.
The tool provides automated red teaming capabilities across three critical domains: Kubernetes security for identifying misconfigurations and privilege escalations, API security for uncovering authentication vulnerabilities, and AI security for testing prompt injection and data poisoning attacks.
Automated Red Teaming for AI, Kubernetes, APIs
“Security vulnerabilities don’t discriminate based on an organization’s size or resources, we believe red teaming should not be a privilege for a few, it should be a foundational practice for all,” said Vrajesh Bhavasar, CEO and co-founder of Operant AI.
The platform specifically addresses modern threats like prompt injection, data poisoning, and model leakage, which have become critical concerns, as only 24% of generative AI projects are currently secured, according to IBM reports.
The technical design of Woodpecker breaks down into three core concepts: Experiments, Verifiers, and Components.
Experiments actively attempt to discover security weaknesses, Verifiers analyze experimental results, and Components are additional applications installed on Kubernetes clusters to enhance functionality.
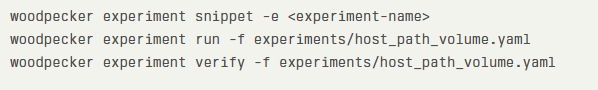
Users can begin testing by running experiments with customizable parameters. The CLI command structure includes:
Components can be installed and managed through YAML configuration files:
The tool supports multiple output formats, including JSON and YAML, for integration into existing security workflows and CI/CD pipelines.
For AI security specifically, Woodpecker covers prompt injection, jailbreaks, model theft, and sensitive data leakage, enabling teams to test malicious prompts from both adversarial and typical users.
Built primarily in Go (94.6%) with Python components (4.3%), Woodpecker is available as a completely free, open-source project on GitHub.
The tool provides compliance mapping for regulatory frameworks including OWASP Top 10 for Kubernetes, APIs, and AI, MITRE ATLAS, and NIST standards.
“The era of reactive security is over, especially with the rise of LLMs and AI agents in live applications,” asserted Dr. Priyanka Tembey, Operant’s co-founder and CTO.
With the Asia Pacific region accounting for over one-third of global cyberattacks in 2024, proactive defense tools like Woodpecker become increasingly vital for organizations of all sizes.
The latest release (version 0.2.0) was published on May 22, 2025, with the project currently maintaining 88 stars and contributions from four developers, including glenn-operant and priyanka-operant.
As part of the launch, Operant AI will host hackathons and developer engagement programs in India, alongside community collaborations with the Coalition for Secure AI.
Live Credential Theft Attack Unmask & Instant Defense – Free Webinar
The post Woodpecker: A Red Teaming Tool for Uncovering Vulnerabilities in AI, Kubernetes, & APIs appeared first on Cyber Security News.
“}]]
Read More Cyber Security News