[[{“value”:”
Cybercriminals have escalated their tactics by exploiting Google Apps Script, a trusted development platform, to host sophisticated phishing campaigns that bypass traditional security measures.
This emerging threat represents a significant shift in how attackers leverage legitimate infrastructure to enhance the credibility of their malicious operations.
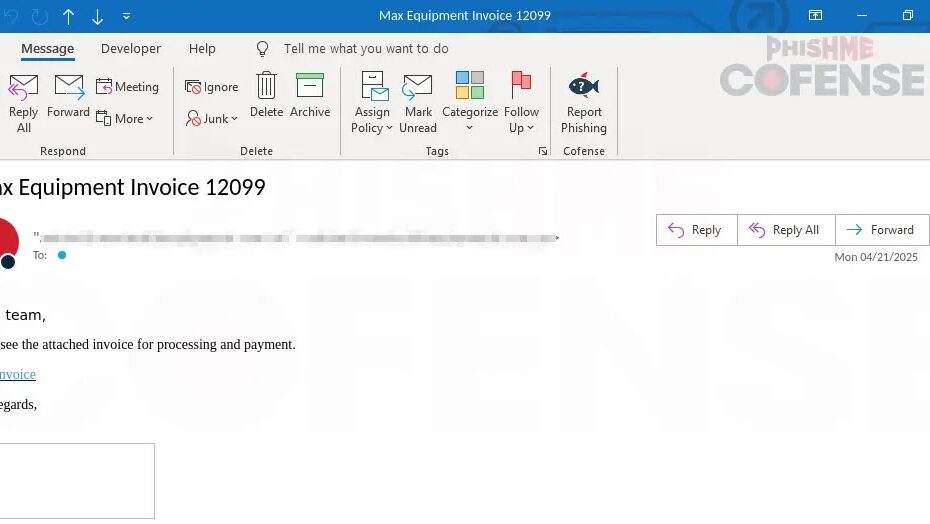
The latest campaign targets unsuspecting users through deceptive invoice emails that appear to originate from legitimate disability and health equipment providers.
These carefully crafted messages contain minimal content to avoid triggering spam filters while creating urgency that prompts immediate action from recipients.
The attackers deliberately exploit the inherent trust users place in communications that appear business-related and time-sensitive.
Cofense analysts identified this sophisticated phishing operation through their Phishing Defense Center, revealing how threat actors have weaponized Google’s own infrastructure to create an illusion of authenticity.
By hosting malicious content on script.google.com domains, attackers effectively circumvent many security solutions that typically whitelist Google services, making detection significantly more challenging for both automated systems and end users.
The campaign’s impact extends beyond simple credential theft, as successful attacks provide cybercriminals with access to corporate email systems and sensitive organizational data.
The use of Google’s trusted environment dramatically increases the likelihood of successful compromise, as users are conditioned to trust Google-hosted content without scrutiny.
Multi-Stage Infection Mechanism
The attack unfolds through a carefully orchestrated sequence designed to maximize victim engagement while minimizing suspicion.
.webp)
Initial infection begins when recipients click the “View Invoice” link in the spoofed email, which redirects them to a Google Apps Script-hosted page displaying what appears to be a legitimate electronic fax download interface.
.webp)
The critical transition occurs when users click the “Preview” button, triggering the deployment of a fraudulent login window that mimics authentic Microsoft authentication interfaces.
.webp)
Once credentials are entered, a PHP script immediately captures and transmits the data to attacker-controlled servers before seamlessly redirecting victims to a legitimate Microsoft login page to maintain the deception.
.webp)
This final redirection serves as psychological camouflage, leaving victims unaware that their credentials have been compromised while providing attackers with immediate access to corporate systems and sensitive information.
Celebrate 9 years of ANY.RUN! Unlock the full power of TI Lookup plan (100/300/600/1,000+ search requests), and your request quota will double.
The post Threat Actors Leverage Google Apps Script To Host Phishing Websites appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News