[[{“value”:”
A comprehensive analysis of the Bitter espionage group has revealed eight years of sustained cyber operations employing increasingly sophisticated custom-developed malware tools designed to evade detection while conducting intelligence gathering activities.
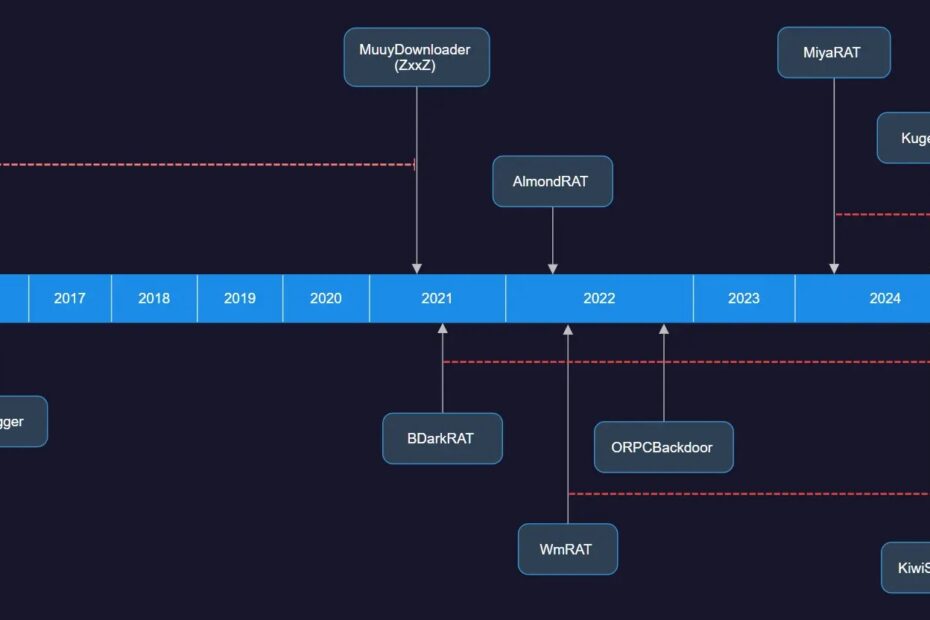
The threat actor, also known as TA397, has demonstrated remarkable persistence and evolution in their attack methodologies, progressing from basic downloaders in 2016 to deploying full-featured Remote Access Trojans (RATs) and advanced evasion techniques by 2025.
.webp)
The Bitter group has primarily targeted victims linked to Pakistan’s foreign affairs and other geopolitically sensitive entities, utilizing spear-phishing campaigns and strategic document-based lures to gain initial access to victim networks.
Their operations span multiple countries and have consistently focused on intelligence collection, suggesting state-sponsored motivations behind their activities.
ThreatRay analysts identified distinctive patterns across Bitter’s malware arsenal that strongly indicate a cohesive development effort spanning nearly a decade.
The researchers discovered that while individual malware families may appear distinct, they share consistent coding practices, particularly in system information gathering routines and string obfuscation techniques.
This analysis, conducted in collaboration with Proofpoint, represents the most comprehensive examination of Bitter’s technical capabilities to date.
The collaborative research effort has led security experts to assess with high confidence that Bitter represents a state-backed threat actor likely operating in the interests of the Indian government.
This conclusion stems from the group’s sustained operational tempo, sophisticated custom tooling, and targeting patterns that align with strategic intelligence priorities.
Evolution of Evasion Techniques and Shared Development Practices
The most striking aspect of Bitter’s operational sophistication lies in their systematic evolution of detection evasion techniques while maintaining consistent development practices across their malware families.
Analysis of their payload arsenal reveals a deliberate progression from simple character-based obfuscation to advanced encryption schemes, demonstrating the group’s adaptive capabilities in response to defensive improvements.
Early malware families such as ArtraDownloader, discovered in 2016, employed basic string obfuscation using simple character arithmetic operations.
The initial variants utilized straightforward encoding where each character was decoded by subtracting predetermined values, typically ranging from 1 to 13 depending on the specific variant.
However, ThreatRay researchers noted that subsequent iterations introduced increasingly complex obfuscation methods, including XOR encryption with unique keys for individual strings and eventually implementing AES-256-CBC encryption in their .NET-based tools.
The group’s commitment to operational security extends beyond mere obfuscation techniques.
.webp)
Their MuuyDownloader family, which replaced ArtraDownloader in 2021, incorporates sophisticated payload delivery mechanisms designed to circumvent network-based detection systems.
The malware deliberately receives payloads with missing PE header bytes, subsequently reconstructing the executable by writing the missing 0x4D byte before execution, effectively evading signature-based network monitoring tools.
Perhaps most significantly, Bitter’s development practices reveal a systematic approach to maintaining operational capabilities while adapting to evolving security measures.
Recent variants of their MiyaRAT family demonstrate this adaptability, with version 5.0 discovered in May 2025 implementing identical functionality to previous iterations while employing modified code patterns specifically designed to defeat signature-based detection.
The researchers observed that while string-based YARA rules failed to detect the latest variant due to newly obfuscated strings, code reuse algorithms successfully identified structural similarities with previous versions.
This evolution pattern suggests that Bitter maintains active development capabilities and continuously monitors defensive responses to their tools, adapting their techniques accordingly while preserving core operational functionality across their expanding malware ecosystem.
Speed up and enrich threat investigations with Threat Intelligence Lookup! -> 50 trial search requests
The post Bitter Malware Using Custom-Developed Tools To Evade Detection In Sophisticated Attacks appeared first on Cyber Security News.
“}]]
Read More .webp) Cyber Security News
Cyber Security News